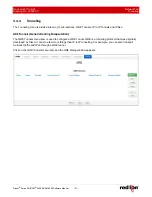
Network Tab
Revised 2017-08-31
Firewall
Drawing No. LP0997-C
- 76 -
Sixnet
®
Series SN/RAM
®
6000 & RAM 9000 Software Manual
To restrict access via a configured whitelist, select a whitelist name for the list of names available in the drop-
down menu.
Note:
This setting will not override any firewall rules defined on other pages, such as service
access or redirect rules.
Whitelist Name:
Select the desired whitelist from the drop-down menu. Whitelists are created in the
Network>Firewall>ACL Rules>Subnet>Whitelist Rules
screen.
SSH:
To allow external devices to connect to the SSH Server, via port 22, through untrusted interfaces on this
unit, select Yes; otherwise select No. The recommended setting for this field is
Yes
.
To restrict access via a configured Whitelist, click the check box marked
Use Whitelist
and then select a
Whitelist name from the list of names available in the drop-down list box provided. Whitelists may be viewed/
defined via the
Network>Firewall>ACL Rules>Subnet Whitelist Rules
screen.
Note:
Setting this option to Yes does not enable the SSH server, it just allows it to be accessible via the
firewall when it is enabled. The SSH Server may be enabled via the
Services>SSH/TELNET Server
screen.
If the SSH Server is configured to use a port other than 22, a rule specifically for the alternate port will need to
be added via the Network>Firewall>Port Allow/Forwarding Rules>Service Access Rules screen.
Note:
This setting will not override any firewall rules defined on other pages, such as service access or
redirect rules.
SSH Whitelist Name:
Select the desired whitelist for the drop-down menu. Whitelists are created in the
Network>Firewall>ACL Rules> Subnet Whitelist Rules
screen.
Telnet:
To allow external devices to connect to the TELNET Server, via port 23, through untrusted interfaces
on this unit, select Yes; otherwise select No. The recommended setting for this field is
No
.
To restrict access via a configured whitelist, click the check box marked Use Whitelist and then select a
whitelist name from the list of names available in the drop-down list box provided. Whitelists may be viewed/
defined via the
Network>Firewall>ACL Rules>Subnet Whitelist Rules
screen.
Note:
Setting this option to Yes does not enable the Telnet Server, it just allows it to be accessible via the
firewall when it is enabled. The Telnet Server may be enabled via the Services>SSH/Telnet Server
Screen.
Note:
This setting will not override any firewall rules defined on other pages, such as service access or
redirect rules.
Telnet Whitelist Name:
Select the desired whitelist for the drop-down menu. Whitelists are created in the
Network>Firewall>ACL Rules> Subnet Whitelist Rules
screen.
Modbus:
To allow external devices to connect to the local MODBUS Server through untrusted interfaces on
this unit, select Yes; otherwise select No. The recommended setting for this field is
No
. This defaults to port
502, but is controlled by the listening port chosen in the
Automation>Modbus>Local Station
screen.
To restrict access via a configured whitelist, click the check box marked
Use Whitelist
and then select a
whitelist name for the list of names available in the drop-down list box provided. Whitelist may be viewed/
defined via the
Network>Firewall>ACL Rules>Subnet Whitelist Rules
screen.
Note:
Setting this option to Yes does not enable the MODBUS server, it just allows it to be accessible via the
firewall when it is enabled. The MODBUS Server may be enabled via the
A
utomation>ModBus>Forwarding
screen.
Modbus Whitelist Name:
Select the desired whitelist for the drop-down menu. Whitelists are created in the
Network>Firewall>ACL Rules> Subnet Whitelist Rules
screen.
DNP3:
To allow external devices to connect to the DNP3 Server, via port 20,000, through untrusted interfaces
on this unit, select Yes; otherwise select No. The recommended setting for this field is
No
.