8 - 12 WiNG 4.4 Switch System Reference Guide
5. Refer to the
Status
field for the current state of the requests made from applet. This field displays error messages if
something goes wrong in the transaction between the applet and the switch.
6. Click the
Refresh
button to update the contents of the screen to the latest values.
7. Click the
Close
button to exit the screen. Clicking Close does not lose any data, as there are no values configured
within this screen (it is view-only).
8.2.2.2 Transferring Log Files
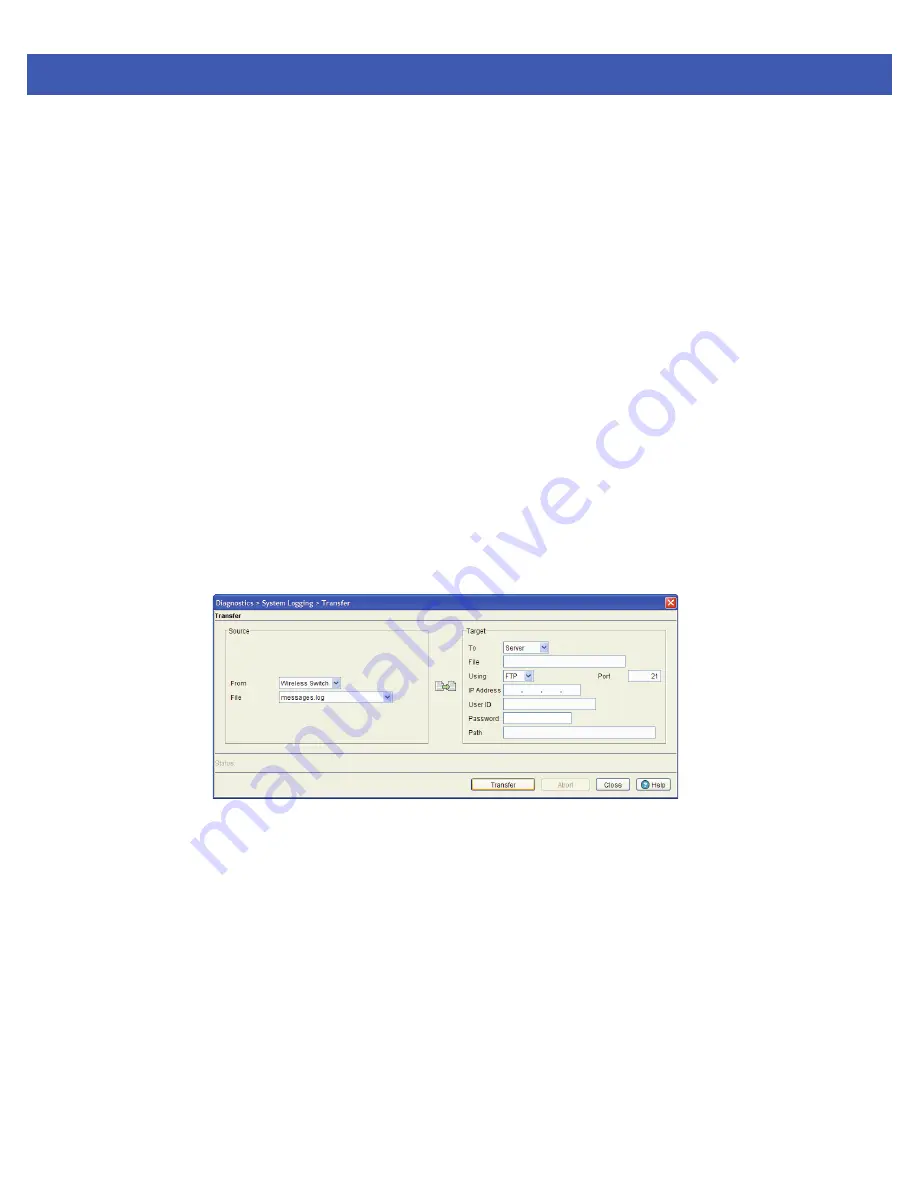
If a system log contains data that may require archiving, consider using the
Transfer Files
screen to export the log file to
an external location (that you designate) where there is no risk of deleting the contents of the log.
To transfer a log file to a user specified location:
1. Select
Diagnostics
>
System Logging
from the main menu tree.
2. Select the
File Mgt
tab.
3. Select a target log file to transfer and click the
Transfer File
button.
4. Use the
From
drop-down menu (within the Source field) to specify the location from which the log file is sent. If only
the applet is available as a transfer location, use the default switch option.
5. Select a target file for transfer from the
File
drop-down menu. The drop-down menu contains the log files listed within
the
File-Mgt
screen.
6. Use the
To
drop-down menu (within the Target field) to define whether the target log file is to be sent to the system's
local disk (Local Disk) or to an external server (Server).
7. Provide the name of the file to be transferred within the
File
parameter. Ensure the file name is correct or the transfer
will not take place.
8. If Server has been selected as the source, use the
Using
drop down-menu to configure whether the log file transfer is
conducted using FTP or TFTP.
9. If Server has been selected as the source, enter the
IP Address
of the destination server or system receiving the log
file. Ensure the IP address is valid or risk jeopardizing the success of the log file transfer.
10.If Server has been selected as the source, enter the
User ID
credentials required to send the log file to the target
location.
Mnemonic
Use the
Mnemonic
as a text version of the severity code information. A
mnemonic is convention for the classification, organization, storage and
recollection of switch information.
Description
Displays a high-level overview of the event, and (when applicable)
message type, error or completion codes for further clarification of the
event. Use this information for troubleshooting or for data collection.
Summary of Contents for WiNG 4.4
Page 1: ...Motorola Solutions WiNG 4 4 SYSTEM REFERENCE GUIDE ...
Page 2: ......
Page 3: ...MOTOROLA SOLUTIONS WING 4 4 SYSTEM REFERENCE GUIDE 72E 157062 01 Revision A January 2012 ...
Page 6: ...iv WiNG 4 4 Switch System Reference Guide ...
Page 14: ...xii WiNG 4 4 Switch System Reference Guide ...
Page 48: ...1 32 WiNG 4 4 Switch System Reference Guide ...
Page 58: ...2 10 WiNG 4 4 Switch System Reference Guide ...
Page 280: ...4 176 WiNG 4 4 Switch System Reference Guide ...
Page 352: ...5 72 WiNG 4 4 Switch System Reference Guide ...
Page 476: ...6 124 WiNG 4 4 Switch System Reference Guide ...
Page 506: ...7 30 WiNG 4 4 Switch System Reference Guide ...
Page 532: ...8 26 WiNG 4 4 Switch System Reference Guide ...
Page 536: ...A 4 WiNG 4 4 Switch System Reference Guide ...
Page 544: ...B 12 WiNG 4 4 Switch System Reference Guide ...
Page 558: ...B 26 WiNG 4 4 Switch System Reference Guide ...
Page 574: ...C 16 WiNG 4 4 Switch System Reference Guide ...
Page 596: ...E 4 WiNG 4 4 Switch System Reference Guide ...
Page 597: ......






























