Example: Configuring MAC RADIUS Authentication on an EX Series Switch
To permit hosts that are not 802.1X-enabled to access the LAN, you can configure MAC
RADIUS authentication on the switch interfaces to which the non-802.1X-enabled hosts
are connected. When MAC RADIUS authentication is configured, the switch will attempt
to authenticate the host with the RADIUS server using the host’s MAC address.
This example describes how to configure MAC RADIUS authentication for two
non-802.1X-enabled hosts:
•
Requirements on page 2564
•
Overview and Topology on page 2564
•
Configuration on page 2566
•
Verification on page 2567
Requirements
This example uses the following hardware and software components:
•
Junos OS Release 9.3 or later for EX Series switches.
•
An EX Series switch acting as an authenticator port access entity (PAE). The ports on
the authenticator PAE form a control gate that blocks all traffic to and from supplicants
until they are authenticated.
•
A RADIUS authentication server. The authentication server acts as the backend
database and contains credential information for hosts (supplicants) that have
permission to connect to the network.
Before you configure MAC RADIUS authentication, be sure you have:
•
Configured basic access between the EX Series switch and the RADIUS server. See
“Example: Connecting a RADIUS Server for 802.1X to an EX Series Switch” on page 2545.
•
Performed basic bridging and VLAN configuration on the switch. See “Example: Setting
Up Basic Bridging and a VLAN for an EX Series Switch” on page 1305.
•
Performed basic 802.1X configuration. See “Configuring 802.1X Interface Settings (CLI
Procedure)” on page 2609.
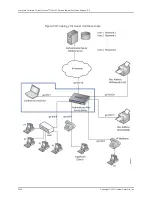
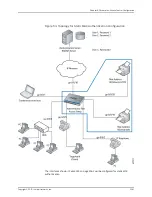
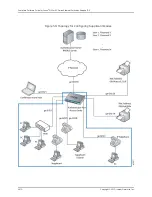
Overview and Topology
IEEE 802.1X Port-Based Network Access Control (PNAC) authenticates and permits
devices access to a LAN if the devices can communicate with the switch using the 802.1X
protocol (are 802.1X-enabled). To permit non-802.1X-enabled end devices to access
the LAN, you can configure MAC RADIUS authentication on the interfaces to which the
end devices are connected. When the MAC address of the end device appears on the
interface, the switch consults the RADIUS server to check whether it is a permitted MAC
address. If the MAC address of the end device is configured as permitted on the RADIUS
server, the switch opens LAN access to the end device.
Copyright © 2010, Juniper Networks, Inc.
2564
Complete Software Guide for Junos
®
OS for EX Series Ethernet Switches, Release 10.3
Summary of Contents for JUNOS OS 10.3 - SOFTWARE
Page 325: ...CHAPTER 17 Operational Mode Commands for System Setup 229 Copyright 2010 Juniper Networks Inc ...
Page 1323: ...CHAPTER 56 Operational Mode Commands for Interfaces 1227 Copyright 2010 Juniper Networks Inc ...
Page 2841: ...CHAPTER 86 Operational Commands for 802 1X 2745 Copyright 2010 Juniper Networks Inc ...
Page 3367: ...CHAPTER 113 Operational Mode Commands for CoS 3271 Copyright 2010 Juniper Networks Inc ...
Page 3435: ...CHAPTER 120 Operational Mode Commands for PoE 3339 Copyright 2010 Juniper Networks Inc ...
Page 3529: ...CHAPTER 126 Operational Mode Commands for MPLS 3433 Copyright 2010 Juniper Networks Inc ...