Appendix B: CC-SG and Network Configuration
353
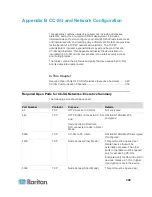
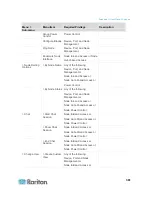
Communication
Direction
Port
Number
Protocol
Configurable?
Details
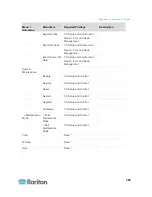
PC Client to CC-SG
443
TCP
no
Client-server communication.
SSL/AES-128/AES-256
encrypted if configured.
PC Client to CC-SG
80
TCP
no
Client-server communication.
Not encrypted. If SSL is
enabled, Port 80 is redirected
to 443.
PC Client to CC-SG
8080
TCP
no
Client-server communication.
SSL/AES-128/AES-256
encrypted if configured.
Port 8080 is open on CC-SG,
not on the PC client.
PC Client to CLI SSH
22
TCP
yes
Client-server communication.
SSL/AES-128/AES-256
encrypted if configured.
PC Client to
Diagnostic Console
23
TCP
yes
Client-server communication.
SSL/AES-128/AES-256
encrypted if configured.
PC Clients to Nodes
Another significant role of CC-SG is to connect PC clients to various
nodes. These nodes can be serial or KVM console connections to
Raritan devices (called Out-of-Band connections). Another mode is to
use In-Band access methods such as VNC, RDP, or SSH.
Another facet of PC client to node communication is whether:
The PC client connects directly to the node either via a Raritan
device or In-Band access. This is called Direct Mode.
The PC client connects to the node through CC-SG, which acts as
an application firewall. This is called Proxy Mode.
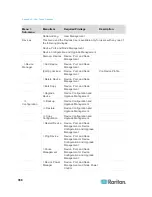
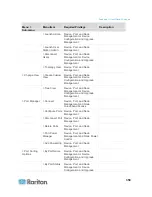
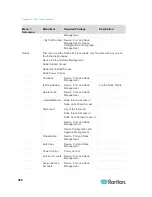
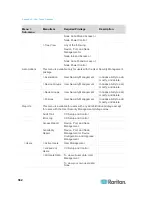
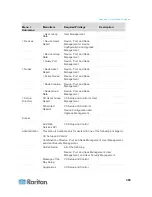
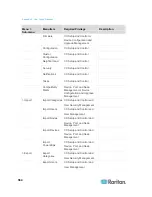
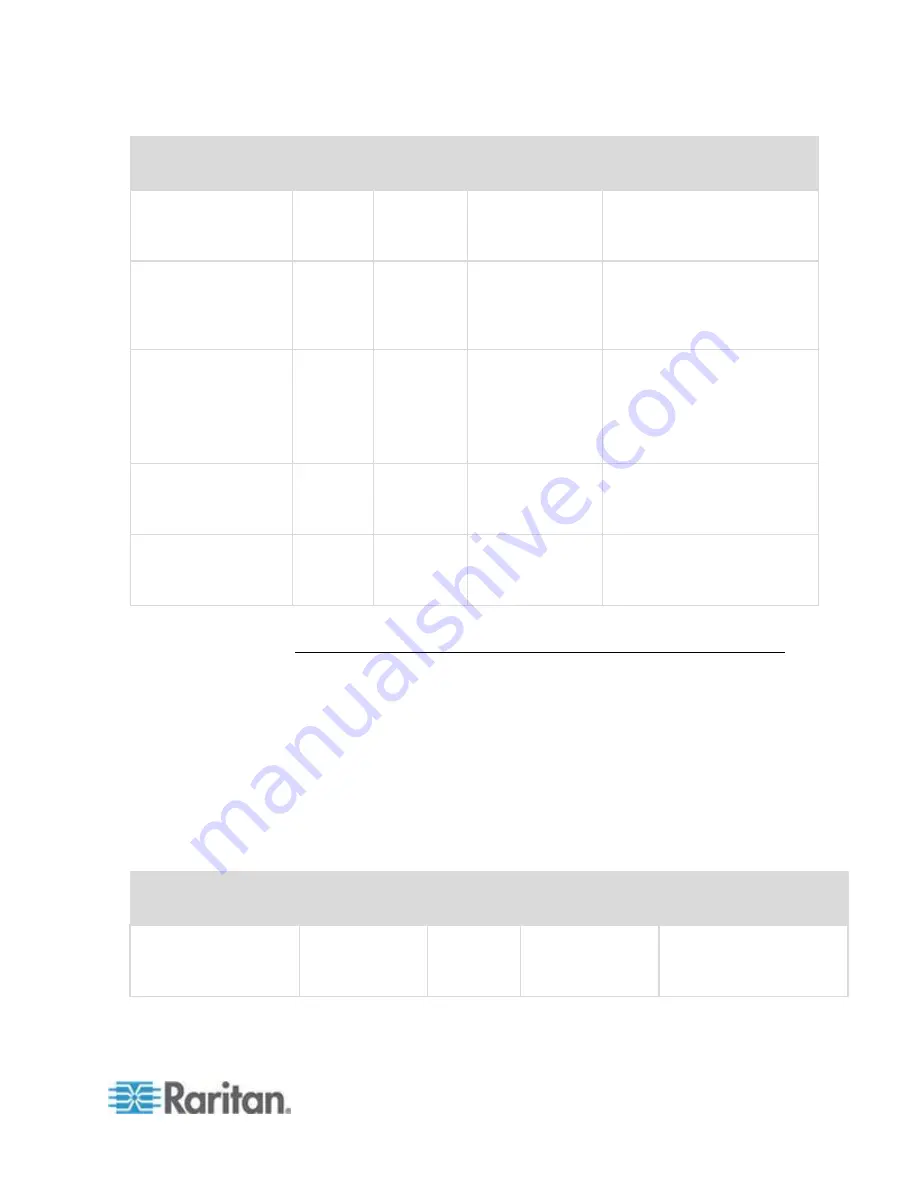
Communication
Direction
Port Number
Protocol
Configurable?
Details
Client to CC-SG via
Proxy to Node
2400
(on CC-SG)
TCP
no
Client-server
communication.
Not encrypted.