Policy Access Domain and Scope
EPICenter Software Installation and User Guide
41
Policy Access Domain and Scope
The policy type and policy traffic definitions specify how to identify a traffic flow of interest. The policy
access domain (Security policy) or scope (IP policy) definition specifies how to handle that traffic flow
on your network devices. The policy access domain or scope definition has three functions: It specifies
the network devices on which the policy should be implemented, what the treatment should be on each
device in the domain or scope.
•
You can specify the domain or scope by selecting individual devices, or you can specify groups to
include in the policy domain or scope.
•
You specify the QoS profile that will be associated with the policy traffic for each resource in the
domain or scope. If you specify a device individually, then you can also specify a QoS profile for that
individual device. However, if you specify a group as a resource, then the QoS profile you select will
apply to the policy traffic on all the devices in the group. If a device is specified more than once in
the domain or scope (for example, because it is a member of two different groups that are both
included in the domain), you can specify which QoS setting will take precedence.
•
You specify the times of validity using the scheduler tool associated with each policy. You can select
which days the policy will be active and you can specify start times and durations for each policy.
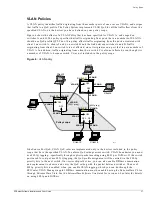
The following example illustrates some of the issues related to setting the scope for an IP policy. Since
the domain for Security policies is limited to the edge device to which the user is connected, many of
these issues are not relevant for Security policies.
Assume that you want to define an IP policy (Access List rule) applying to all TCP traffic (in both
directions) between Host1 and Host2. This defines two traffic flows for the policy:
•
From any L4 port on Host1 to any L4 port on Host2
•
From any L4 port on Host2 to any L4 port on Host1
Initially, you decide to define the scope as follows:
•
Include all the devices on your network (switches A, B, and C) in the scope
•
Set QP1 as the profile to be used on all three devices
This means that any time any of these switches detects TCP traffic with Host1 as the source and Host2
as the destination (or vice-versa), it will assign that traffic to profile QP1.
However, in your network it happens that traffic between Host1 and Host2 would never travel through
switch C, so implementing this policy on that switch is not necessary. Further, on switch B, profile QP1
is being used for some very high-priority, application-server traffic, so you want to give your TCP traffic
somewhat lower priority on that switch. You can accomplish this by changing the policy scope as
follows:
•
Include only switches A and B in your policy scope. This will leave switch C unaffected by this
policy.
•
Specify profile QP1 for switch A, but a different profile (for example, QP3) for switch B. On switch B,
you configure profile QP3 to have the appropriate parameters to accomplish the desired traffic
prioritization.
Alternatively, it might happen that the high priority traffic on switch B is not using QP1, so you can use
QP1 on both switches for the Host1-Host2 traffic. However, you may need to set the parameters for QP1
on switch B differently from the parameters of QP1 on switch A, to accomplish the desired traffic
priorities on switch B.
Summary of Contents for EPICenter 4.1
Page 20: ...20 EPICenter Software Installation and User Guide Preface ...
Page 46: ...46 EPICenter Software Installation and User Guide EPICenter and Policy Manager Overview ...
Page 190: ...190 EPICenter Software Installation and User Guide Configuration Manager ...
Page 204: ...204 EPICenter Software Installation and User Guide Using the Interactive Telnet Application ...
Page 242: ...242 EPICenter Software Installation and User Guide Using the IP MAC Address Finder ...
Page 266: ...266 EPICenter Software Installation and User Guide Using ExtremeView ...
Page 284: ...284 EPICenter Software Installation and User Guide Real Time Statistics ...
Page 436: ...436 EPICenter Software Installation and User Guide Using the Policy Manager ...
Page 454: ...454 EPICenter Software Installation and User Guide The ACL Viewer ...
Page 468: ...468 EPICenter Software Installation and User Guide Troubleshooting ...
Page 504: ...504 EPICenter Software Installation and User Guide EPICenter External Access Protocol ...
Page 510: ...510 EPICenter Software Installation and User Guide EPICenter Database Views ...
Page 522: ...522 EPICenter Software Installation and User Guide EPICenter Backup ...
Page 526: ...526 EPICenter Software Installation and User Guide Dynamic Link Context System DLCS ...
Page 546: ......