A Port Grouping Includes the IP Address
If a grouping by port is selected then this implicitly also includes the IP address. For example,
port 1024 of host computer A is not the same as port 1024 of host computer B. It is the
combination of port and IP address that identifies a unique user in a group.
Grouping by Networks Requires the Size
If the grouping is by source or destination network then the network size must also be specified
In other words, the netmask for the network must be specified for NetDefendOS.
Specifying Group Limits
Once the way the method of grouping is selected, the next step is to specify the Group Limits.
These limits can consist of one or both of the following:
•
Group Limit Total
This value specifies a limit for each user within the grouping. For example, if the grouping is
by source IP address and the total specified is 100 Kbps then this is saying that no one IP
address can take more than 100 Kbps of bandwidth.
•
Group Precedence Guarantees
In addition to, or as an alternative to the total group limit, individual precedences can have
values specified. These values are, in fact,
guarantees
(not limits) for each user in a group. For
example, precedence 3 might have the value 50 Kbps and this is saying that an individual
user (in other words, each source IP if that is the selected grouping) with that precedence will
be guaranteed 50 Kbps at the expense of lower precedences.
The precedences for each user must be allocated by different pipe rules that trigger on
particular users. For example, if grouping is by source IP then different pipe rules will trigger
on different IPs and send the traffic into the same pipe with the appropriate precedence.
The potential sum of the precedence values could clearly become greater than the capacity
of the pipe in some circumstances so it is important to specify the total pipe limit when using
these guarantees.
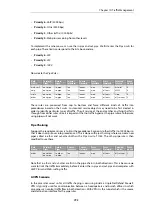
Combining the Group Total and Precedences
Use of group precedences and the group total can be combined. This means that:
•
The users in a group are first separated by pipe rules into precedences.
•
The users are then subject to the guarantees specified for their precedence.
•
The combined traffic is subject to the total group limit.
The illustration below shows this flow where the grouping has been selected to be according to
source IP.
Chapter 10: Traffic Management
789
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...