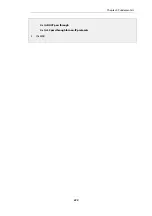
Example 3.24. 6in4 Tunnel Configuration
In this example, a
6in4 Tunnel
object will be configured to connect with a remote tunnel server
across the public Internet.
It is assumed that a number of address objects have already been configured in the
NetDefendOS address book. These have the names
local_endpoint_ip6
for the local inner IPv6
endpoint of the tunnel and
tunnel_server_ip4
for the IPv4 address of the tunnel server.
Command-Line Interface
gw-world:/> add Interface IP6in4Tunnel my_6in4_tunnel
IP=local_endpoint_ip6
Network=all-nets6
RemoteEnpoint=tunnel_server_ip4
Web Interface
1.
Go to: Network > Interfaces and VPN > 6in4 > Add > 6in4 Tunnel
2.
Enter the following:
•
Name: my_6in4_tunnel
•
IP Address: local_endpoint_ip6
•
Remote Network: all-nets6
•
Remote Endpoint: tunnel_server_ip4
3.
Click OK
Routing Table Usage with 6in4 Tunnels
By default, the lookup of the IPv4 remote endpoint is done in the NetDefendOS
main
routing
table. This can be changed to be a specific routing table. The route for the
Remote Network
property of the tunnel is also added, by default, to all routing tables including the
main
table.
This can also be changed so that the addition is made to a specific routing table.
MTU resizing
The MTU used by the protected IPv6 clients should not be too large since this will result in
excessive fragmentation during the tunneling process and thereby introduce unnecessary
overhead. There are two ways that the IPv6 clients behind a firewall can have their MTU value
adjusted:
•
If the Pass returned ICMP error messages from destination property is enabled for the
Service
objects used by the IP rules or IP policies controlling traffic flow, the IPv6 hosts will
initially take on the default MTU property of the
6in4 Tunnel
object. By default this is
1280
which is the minimum value for IPv6. If other downstream network equipment requires a
different MTU, this can also be communicated via ICMP messages.
•
A NetDefendOS
Router Advertisement
object can be configured on the interface connected to
Chapter 3: Fundamentals
211
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...