route in its routing tables for the destination.
The key aspect of an OSPF setup is that connected NetDefend Firewalls share the information in
their routing tables so that traffic entering an interface on one of the firewalls can be
automatically routed so that it exits the interface on another gateway which is attached to the
correct destination network.
Another important aspect is that the firewalls monitor the connections between each other and
route traffic by an alternate connection if one is available. A network topology can therefore be
designed to be fault tolerant. If a connection between two firewalls fails then any alternate route
that also reaches the destination will be used.
4.6.3. OSPF Components
This section looks at the NetDefendOS objects that need to be configured for OSPF routing.
Defining these objects creates the OSPF network. The objects should be defined on each
NetDefend Firewall that is part of the OSPF network and should describe the same network.
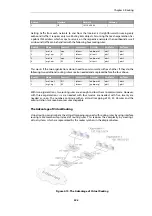
An illustration of the relationship between NetDefendOS OSPF objects is shown below.
Figure 4.15. NetDefendOS OSPF Objects
4.6.3.1. OSPF Router Process
This object defines the
autonomous system
(AS) which is the top level of the OSPF network. A
similar
Router Process
object should be defined on each NetDefend Firewall which is part of the
OSPF network.
General Parameters
Name
Specifies a symbolic name for the OSPF AS.
Router ID
Specifies the IP address that is used to identify the router in a
AS. If no Router ID is configured, the firewall computes the
Router ID based on the highest IP address of any interface
Chapter 4: Routing
339
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...