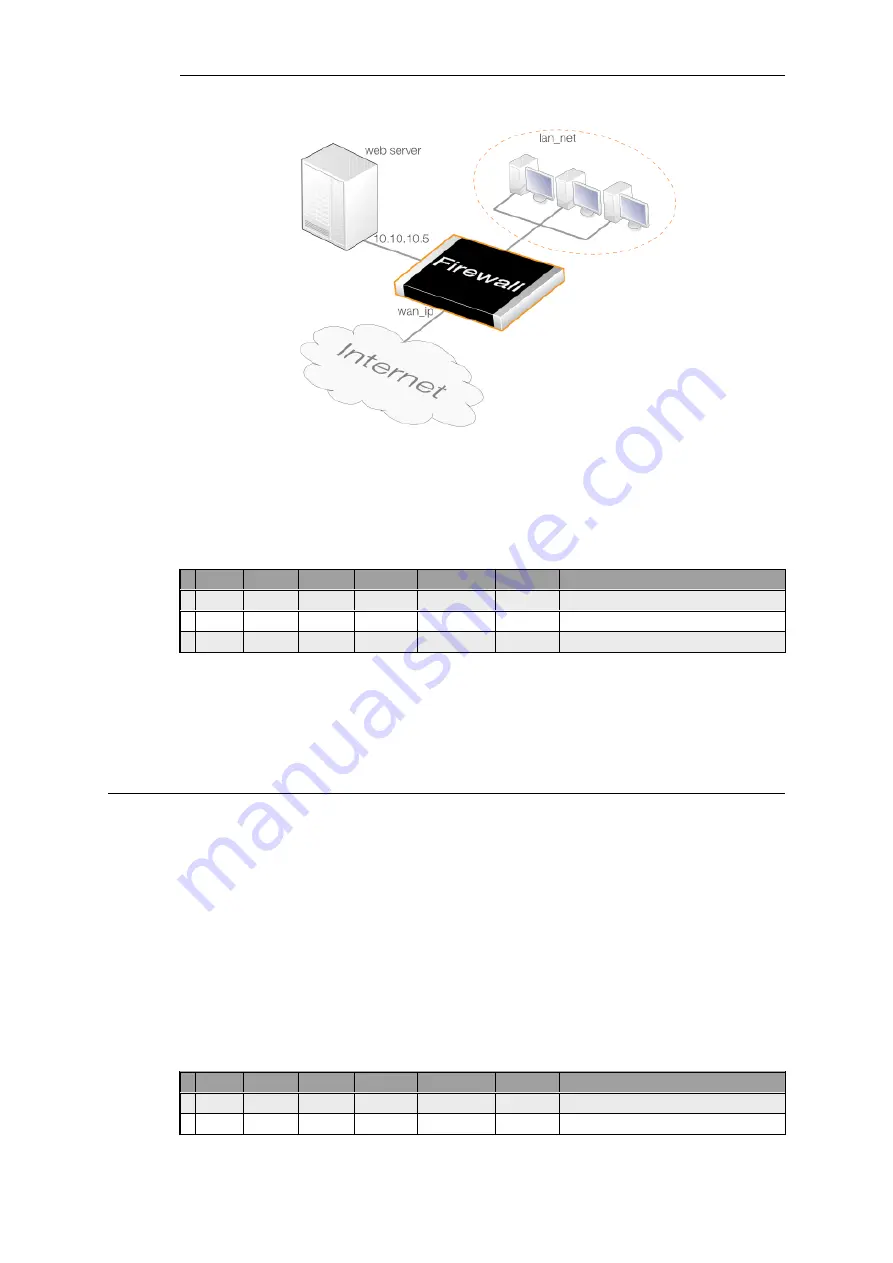
Figure 7.5. SAT Address Translation
If internal clients require access to the public Internet, a NAT rule is also needed and the source
interface of the
SAT
rule must be set to
any
. The correct second rule for the external or internal
traffic is then selected based on the source interface.
# Action
Src Iface
Src Net
Dest Iface Dest Net
Service
SAT Action
1 SAT
any
all-nets
core
wan_ip
http-all
Destination IP: 10.10.10.5
2 Allow
wan
all-nets
core
wan_ip
http-all
3 NAT
lan
lan_net
any
all-nets
http-all
Here, only one
SAT
rule is needed and once it triggers it will be used with whichever rule is
triggered next. The ordering of the
Allow
and
NAT
rules does not matter but they must be found
after the
SAT
rule.
If the web server is on the same network as the client, a different approach is required where the
SAT
rule is paired with a
NAT
rule and this is described later in
7.4.3. Many-to-Many IP Translation
A single
SAT
rule can be used to transpose an entire range or network of IP addresses to another
range or network. The result is a
many-to-many translation
where the first original IP address is
translated to the first IP address in the new range or network, then the second to the second, and
so on.
To tell NetDefendOS to perform this type of translation, the original IP address must be a range
or network and the IP rule's
All to One
property must be disabled. The new range or network is
specified using a single IP address which is the starting address for the transposition. For
example,
192.168.1.0
would be specified as the new address if the transposition is to the network
192.168.1.0/24
and starting from the first address in the network.
As another example, a SAT IP rule might specify that connections to the
194.1.2.16/29
network
should be translated to
192.168.0.50
. The IP rules for this would be:
# Action
Src Iface
Src Net
Dest Iface Dest Net
Service
SAT Action
1 SAT
any
all-nets
core
194.1.2.16/29 all_services Destination IP: 192.168.0.50
2 Allow
any
all-nets
core
194.1.2.16/29 all_services
Chapter 7: Address Translation
593
Содержание NetDefendOS
Страница 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Страница 32: ...Chapter 1 NetDefendOS Overview 32 ...
Страница 144: ...Chapter 2 Management and Maintenance 144 ...
Страница 220: ... Enable DHCP passthrough Enable L2 passthrough for non IP protocols 4 Click OK Chapter 3 Fundamentals 220 ...
Страница 267: ... SourceNetwork lannet DestinationInterface any DestinationNetwork all nets 4 Click OK Chapter 3 Fundamentals 267 ...
Страница 284: ...Chapter 3 Fundamentals 284 ...
Страница 360: ...The ospf command options are fully described in the separate NetDefendOS CLI Reference Guide Chapter 4 Routing 360 ...
Страница 392: ...Chapter 4 Routing 392 ...
Страница 396: ...Web Interface 1 Go to Network Ethernet If1 2 Select Enable DHCP 3 Click OK Chapter 5 DHCP Services 396 ...
Страница 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Страница 420: ...Chapter 5 DHCP Services 420 ...
Страница 424: ...2 Now enter Name lan_Access Action Expect Interface lan Network lannet 3 Click OK Chapter 6 Security Mechanisms 424 ...
Страница 573: ...Chapter 6 Security Mechanisms 573 ...
Страница 575: ...This section describes and provides examples of configuring NAT and SAT rules Chapter 7 Address Translation 575 ...
Страница 607: ...Chapter 7 Address Translation 607 ...
Страница 666: ...Chapter 8 User Authentication 666 ...
Страница 775: ...Chapter 9 VPN 775 ...
Страница 819: ...Chapter 10 Traffic Management 819 ...
Страница 842: ...Chapter 11 High Availability 842 ...
Страница 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Страница 879: ...Chapter 13 Advanced Settings 879 ...



































