330
•
UC-P100-S/UC-P110-S Phones for Skype for Business
Supplemental Guide – DOC. 8412A
Select the maximum amount of unlock attempts from the Max attempts of
unlock drop-down list.
Click Confirm to accept the changes.
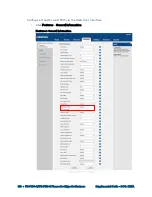
Configure Phone Lock via the Phone User Interface
Tap Setting > Basic > Phone Lock.
Configure the fields as needed.
Tap Save.
Transport Layer Security (TLS)
TLS is a commonly-used protocol for providing communications privacy and managing
the security of message transmission, allowing Skype for Business phones to
communicate with other remote parties and connect to the HTTPS URL for provisioning
in a way that is designed to prevent eavesdropping and tampering.
TLS protocol is composed of two layers: TLS Record Protocol and TLS Handshake
Protocol. The TLS Record Protocol completes the actual data transmission and ensures
the integrity and privacy of the data. The TLS Handshake Protocol allows the server and
client to authenticate each other and negotiate an encryption algorithm and
cryptographic keys before data is exchanged.
The TLS protocol uses asymmetric encryption for authentication of key exchange,
symmetric encryption for confidentiality, and message authentication codes for
integrity.
•
Symmetric encryption: For symmetric encryption, the encryption key and the
corresponding decryption key can be told by each other. In most cases, the
encryption key is the same as the decryption key.
•
Asymmetric encryption: For asymmetric encryption, each user has a pair of
cryptographic keys – a public encryption key and a private decryption key. The
information encrypted by the public key can only be decrypted by the
corresponding private key and vice versa. Usually, the receiver keeps its private
key. The public key is known by the sender, so the sender sends the information
encrypted by the known public key, and then the receiver uses the private key to
decrypt it.
Skype for Business phones support TLS version 1.0, 1.1 and 1.2. A cipher suite is a named
combination of authentication, encryption, and message authentication code (MAC)
algorithms used to negotiate the security settings for a network connection using the
TLS/SSL network protocol. IP phones support the following cipher suites:
•
DHE-RSA-AES256-SHA
•
DHE-DSS-AES256-SHA
•
AES256-SHA
•
EDH-RSA-DES-CBC3-SHA