RUGGEDCOM ROX II
User Guide
Chapter 5
Setup and Configuration
Configuring the Firewall for a VPN
373
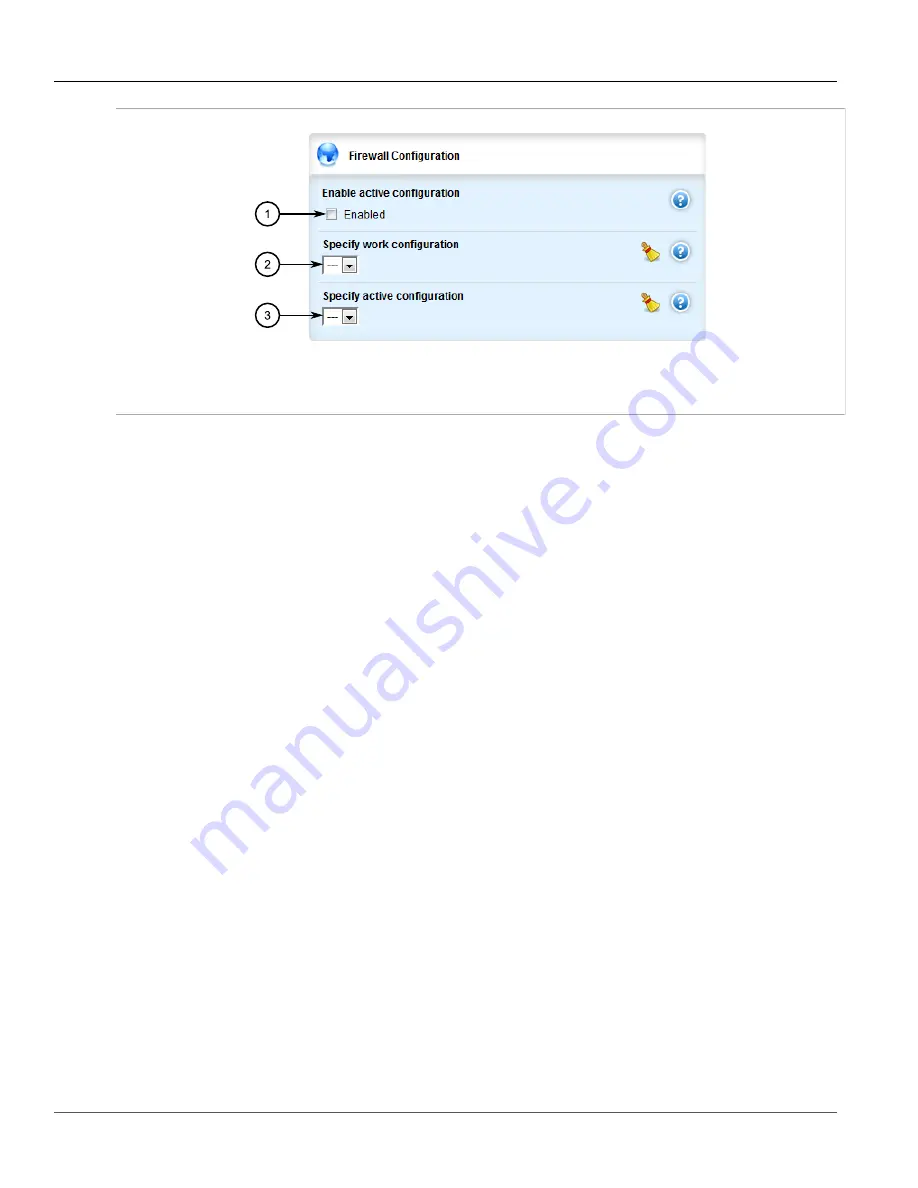
Figure 407: Firewall Configuration Form
1.
Enable Active Configuration Check Box
2.
Specify Work Configuration List
3.
Specify Active Configuration List
3. Under
Specify work configuration
, select a firewall configuration from the list to work on. The firewall
configuration selected under
Specify active configuration
is the configuration that is actively running.
4. Click
Commit
to save the changes or click
Revert All
to abort. A confirmation dialog box appears. Click
OK
to proceed.
5. Click
Exit Transaction
or continue making changes.
Section 5.17.6
Configuring the Firewall for a VPN
To configure the firewall for a policy-based VPN, do the following:
1. Click
Tools
on the toolbar followed by
CLI
. The CLI terminal window appears.
2. Make sure a basic firewall has been configured. For more information about configuring a firewall, refer to
Section 5.17.3, “Adding a Firewall”
.
3. Change the mode to
Edit Private
or
Edit Exclusive
.
4. Navigate to
security
»
firewall
»
fwconfig
and select the firewall to configure.
5. Make sure zones for local, network and VPN traffic have been configured. For more information about
managing zones, refer to
Section 5.17.8, “Managing Zones”
6. Make sure a zone called
Any
exists and is of the type IPsec . For more information about managing zones,
refer to
Section 5.17.8, “Managing Zones”
.
7. Configure the interface that carries the encrypted IPsec traffic. Make sure it is associated with the
Any
zone,
as it will be carrying traffic for all zones. For more information about associating interfaces with zones, refer
to
Section 5.17.9.3, “Associating an Interface with a Zone”
8. Configure a host for the interface that carries the encrypted IPsec traffic. Make sure the VPN zone is
associated with the interface. If VPN tunnels to multiple remote sites are required, make sure host entry
exists for each or collapse them into a single subnet. For more information about configuring hosts, refer to
Section 5.17.10, “Managing Hosts”
9. Configure a second host for the interface that carries the encrypted IPsec traffic. Make sure the interface is
associated with the network zone and specify a wider subnet mask, such as 0.0.0.0/0. For more information
about configuring hosts, refer to
Summary of Contents for RUGGEDCOM RX1510
Page 32: ...RUGGEDCOM ROX II User Guide Preface Customer Support xxxii ...
Page 44: ...RUGGEDCOM ROX II User Guide Chapter 1 Introduction User Permissions 12 ...
Page 62: ...RUGGEDCOM ROX II User Guide Chapter 2 Using ROX II Using the Command Line Interface 30 ...
Page 268: ...RUGGEDCOM ROX II User Guide Chapter 4 System Administration Deleting a Scheduled Job 236 ...






























