•
A control flow transitions into a suspicious state; another trap and log message is
generated on removal from a suspicious state.
•
A protocol transitions to or from the suspicious state.
•
A priority transitions to or from the suspicious state.
•
The suspicious flow control system is overflowing or grouping flows on a line module.
You can control trap and log messages using CLI or SNMP commands.
Suspicious Control Flow Commands
Use the commands described in this section to regulate suspicious control flows.
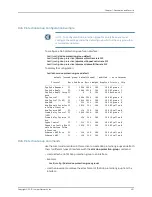
baseline suspicious-control-flow-detection counts
•
Use to set a baseline for statistics for suspicious control flow detection.
•
Example
host1#
baseline suspicious-control-flow-detection counts
•
There is no
no
version.
•
See baseline suspicious-control-flow-detection counts.
clear suspicious-control-flow-detection
•
Use to clear the active state for suspicious control detection.
•
If you do not specify a slot or interface, clears all suspicious flows.
•
If you specify a slot, clears all specified suspicious flows on that slot.
•
If you specify an interface and protocol, and source mac-address, clears that specific
flow.
•
Example
host1#
clear suspicious-control-flow-detection interface atm 1/0.1 ppp Control address
0000.0001.0002
•
There is no
no
version.
•
See clear suspicious-control-flow-detection.
suspicious-control-flow-detection grouping-off
•
Use to turn off overflow protection for suspicious control flow detection, enabling flows
to be grouped into larger entities when the line module flow table overflows.
•
Example
host1(config)#
suspicious-control-flow-detection grouping-off
•
Use the
no
version to turn on overflow protection.
•
See suspicious-control-flow-detection grouping-off.
suspicious-control-flow-detection off
439
Copyright © 2010, Juniper Networks, Inc.
Chapter 7: Passwords and Security
Summary of Contents for JUNOSE 11.3
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 8: ...Copyright 2010 Juniper Networks Inc viii JunosE 11 3 x System Basics Configuration Guide...
Page 24: ...Copyright 2010 Juniper Networks Inc xxiv JunosE 11 3 x System Basics Configuration Guide...
Page 32: ...Copyright 2010 Juniper Networks Inc 2 JunosE 11 3 x System Basics Configuration Guide...
Page 146: ...Copyright 2010 Juniper Networks Inc 116 JunosE 11 3 x System Basics Configuration Guide...
Page 166: ...Copyright 2010 Juniper Networks Inc 136 JunosE 11 3 x System Basics Configuration Guide...
Page 432: ...Copyright 2010 Juniper Networks Inc 402 JunosE 11 3 x System Basics Configuration Guide...
Page 488: ...Copyright 2010 Juniper Networks Inc 458 JunosE 11 3 x System Basics Configuration Guide...
Page 524: ...Copyright 2010 Juniper Networks Inc 494 JunosE 11 3 x System Basics Configuration Guide...
Page 554: ...Copyright 2010 Juniper Networks Inc 524 JunosE 11 3 x System Basics Configuration Guide...
Page 566: ...Copyright 2010 Juniper Networks Inc 536 JunosE 11 3 x System Basics Configuration Guide...
Page 588: ...Copyright 2010 Juniper Networks Inc 558 JunosE 11 3 x System Basics Configuration Guide...
Page 613: ...PART 3 Index Index on page 585 583 Copyright 2010 Juniper Networks Inc...
Page 614: ...Copyright 2010 Juniper Networks Inc 584 JunosE 11 3 x System Basics Configuration Guide...
Page 632: ...Copyright 2010 Juniper Networks Inc 602 JunosE 11 3 x System Basics Configuration Guide...