The server encodes SNMP responses using the same SNMP version received in the
corresponding request and encodes traps using the SNMP version configured for the trap
recipient.
SNMPv2c supports the capabilities defined for SNMPv1 and provides greater power and
flexibility through the addition of several features, including:
•
More detailed error codes
•
GetBulk operation for efficient retrieval of large amounts of data
•
64-bit counters
SNMPv3 is an extensible SNMP framework that supplements the SNMPv2c framework
by supporting:
•
Security for messages
•
Explicit access control
Security Features
As users transfer more sensitive information, such as billing details, through the Internet,
security becomes more critical for SNMP and other protocols. SNMPv3 provides the
user-based security model (USM) to address authentication and data encryption.
Authentication provides the following benefits:
•
Only authorized parties can communicate with each other. Consequently, a
management station can interact with a device only if the administrator configured
the device to allow the interaction.
•
Messages are received promptly; users cannot save messages and replay them to alter
content. This feature prevents users from sabotaging SNMP configurations and
operations. For example, users can change configurations of network devices only if
authorized to do so.
SNMPv3 authenticates users through the HMAC-MD5-96 or HMAC-SHA-96 protocols;
CBC-DES is the encryption or privacy protocol. The SNMP agent recognizes up to 32
usernames that can have one of the following security levels:
•
No authentication and no privacy (none)
•
Authentication only (auth only)
•
Authentication and privacy (priv)
In contrast, SNMPv1and SNMPv2c provide only password protection, through the
community name and IP address. When an SNMP server receives a request, the server
extracts the client’s IP address and the community name. The SNMP community table
is searched for a matching community. If a match is found, its access list, if nonzero, is
used to validate the IP address. If the access list number is zero, the IP address is accepted.
A nonmatching community or an invalid IP address causes an SNMP authentication error.
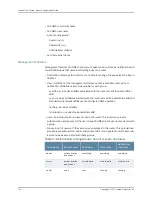
Each entry in the community table identifies:
141
Copyright © 2010, Juniper Networks, Inc.
Chapter 4: Configuring SNMP
Summary of Contents for JUNOSE 11.3
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 8: ...Copyright 2010 Juniper Networks Inc viii JunosE 11 3 x System Basics Configuration Guide...
Page 24: ...Copyright 2010 Juniper Networks Inc xxiv JunosE 11 3 x System Basics Configuration Guide...
Page 32: ...Copyright 2010 Juniper Networks Inc 2 JunosE 11 3 x System Basics Configuration Guide...
Page 146: ...Copyright 2010 Juniper Networks Inc 116 JunosE 11 3 x System Basics Configuration Guide...
Page 166: ...Copyright 2010 Juniper Networks Inc 136 JunosE 11 3 x System Basics Configuration Guide...
Page 432: ...Copyright 2010 Juniper Networks Inc 402 JunosE 11 3 x System Basics Configuration Guide...
Page 488: ...Copyright 2010 Juniper Networks Inc 458 JunosE 11 3 x System Basics Configuration Guide...
Page 524: ...Copyright 2010 Juniper Networks Inc 494 JunosE 11 3 x System Basics Configuration Guide...
Page 554: ...Copyright 2010 Juniper Networks Inc 524 JunosE 11 3 x System Basics Configuration Guide...
Page 566: ...Copyright 2010 Juniper Networks Inc 536 JunosE 11 3 x System Basics Configuration Guide...
Page 588: ...Copyright 2010 Juniper Networks Inc 558 JunosE 11 3 x System Basics Configuration Guide...
Page 613: ...PART 3 Index Index on page 585 583 Copyright 2010 Juniper Networks Inc...
Page 614: ...Copyright 2010 Juniper Networks Inc 584 JunosE 11 3 x System Basics Configuration Guide...
Page 632: ...Copyright 2010 Juniper Networks Inc 602 JunosE 11 3 x System Basics Configuration Guide...