391
Providing remote access using VPN tunnels
Configuring tunnels
12
Click
Next
.
13
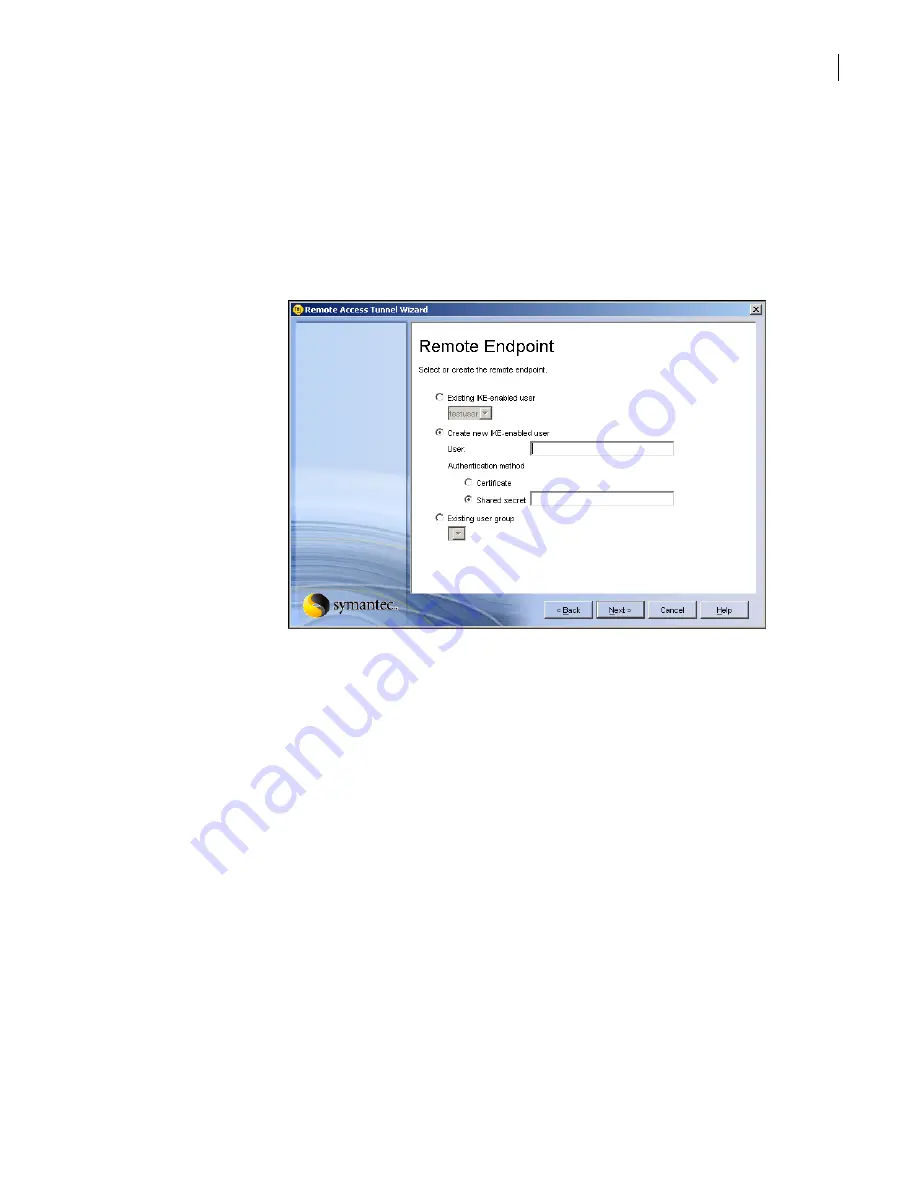
In the Remote Endpoint panel, do one of the following:
■
To use an existing IKE-enabled user as the remote tunnel endpoint, click
Existing IKE-
enabled user
and select the existing user from the drop-down list.
■
To create a new IKE-enabled user to serve as the remote tunnel endpoint, click
Create new
IKE-enabled user
, and then do the following:
■
To use an existing user group as the remote tunnel endpoint, click
Existing user group
and
select the existing user group from the drop-down list.
If you are using a user group as the remote endpoint, you need to edit the user group
properties to enable the primary IKE user group.
14
Click
Next
.
15
In the VPN Policy panel, in the drop-down list, select a VPN policy.
16
Click
Next
.
For a Subnet network
entity:
■
In the Name text box, type a name for the new endpoint.
■
In the Subnet IP address, type the IP address or fully-qualified domain name of
the new endpoint.
■
In the Netmask text box, type the netmask for the subnet.
For a Group network
entity:
■
In the Group Name text box, type a name for the new endpoint.
■
In the Existing Network Entities list box, select the network entities to include
in the group network entity.
User
In the User text box, type the user name.
Do not include spaces in the name.
Authentication
method
To specify the means of authentication, select either
Certificate
or
Shared
secret
. You must use the same authentication method on both ends of the VPN
tunnel.
Shared secret
If you are using a shared secret, type it in the text box.
Summary of Contents for Security 5600 Series, Security 5400 Series,Clientless VPN 4400 Series
Page 76: ...76 Managing administrative access Enabling SSH for command line access to the appliance...
Page 242: ...242 Defining your security environment Controlling full application inspection of traffic...
Page 243: ...243 Defining your security environment Controlling full application inspection of traffic...
Page 269: ...268 Limiting user access Authenticating using Out Of Band Authentication OOBA...
Page 373: ...372 Preventing attacks Enabling protection for logical network interfaces...
Page 509: ...508 Generating reports Upgrade reports...
Page 553: ...552 Advanced system settings Configuring advanced options...
Page 557: ...556 SSL server certificate management Installing a signed certificate...
Page 861: ...860 Index...






























