Exinda Network Orchestrator
3 Using
|
280
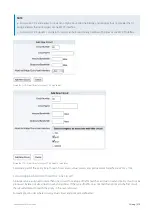
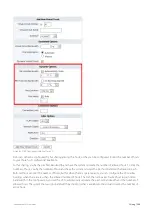
Screenshot 129: Setting options for a virtual circuit.
Network objects are typically used when virtual circuits are created for specific branch office locations, or other subsets of
the network, or user groups. Each branch office location or user group would be represented by a static network object
or a dynamic network object (such as an Active Directory group). A default network object, private net, exists which
defines all non-routable subnets. This can be used to create a virtual circuit for all WAN data.
The direction is used to ensure that the virtual circuit only captures traffic in a certain direction. This is useful for
asymmetric circuits, as these generally require that at least two virtual circuits are defined - one for the inbound
bandwidth and one for the outbound bandwidth.
Virtual circuits are part of the policy tree. To learn how circuits, virtual circuits, and policies work together, see
Related Topics
Creating a new Virtual Circuit
How to handle oversubscription in a Virtual Circuit
Configuring a Virtual Circuit as a Dynamic Virtual Circuit
Ensuring minimum bandwidth when sharing equally
Capping bandwidth usage per host
Capping bandwidth usage per host with minimum bandwidth
Summary of Contents for EXNV-10063
Page 369: ...Exinda Network Orchestrator 4 Settings 369 ...
Page 411: ...Exinda Network Orchestrator 4 Settings 411 Screenshot 168 P2P OverflowVirtualCircuit ...
Page 420: ...Exinda Network Orchestrator 4 Settings 420 Screenshot 175 Students OverflowVirtualCircuit ...