802.1X |
109
•
The
authentication-server
selects the authentication method, verifies the information provided by the
supplicant, and grants it network access privileges.
Ports can be in one of two states:
•
Ports are in an
unauthorized
state by default. In this state, non-802.1X traffic cannot be forwarded in
or out of the port.
•
The authenticator changes the port state to
authorized
if the server can authenticate the supplicant. In
this state, network traffic can be forwarded normally.
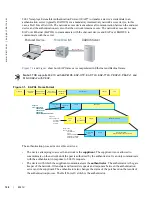
The Port-authentication Process
The authentication process begins when the authenticator senses that a link status has changed from down
to up:
1. When the authenticator senses a link state change, it requests that the supplicant identify itself using an
EAP Identity Request Frame.
2. The supplicant responds with its identity in an EAP Response Identity frame.
3. The authenticator decapsulates the EAP Response from the EAPOL frame, encapsulates it in a
RADIUS Access-Request frame, and forwards the frame to the authentication server.
4. The authentication server replies with an Access-Challenge. The Access-Challenge is request that the
supplicant prove that it is who it claims to be, using a specified method (an EAP-Method). The
challenge is translated and forwarded to the supplicant by the authenticator.
5. The supplicant can negotiate the authentication method, but if it is acceptable, the supplicant provides
the requested challenge information in an EAP Response, which is translated and forwarded to the
authentication server as another Access-Request.
6. If the identity information provided by the supplicant is valid, the authentication server sends an
Access-Accept frame in which network privileges are specified. The authenticator changes the port
state to authorized, and forwards an EAP Success frame. If the identity information is invalid, the
server sends and Access-Reject frame. The port state remains unauthorized, and the authenticator
forwards EAP Failure frame.
Note:
The Dell Force10 switches place 802.1X-enabled ports in the unauthorized state by default.
Summary of Contents for Force10 E300
Page 1: ...FTOS Configuration Guide FTOS 8 4 2 7 E Series TeraScale C Series S Series S50 S25 ...
Page 32: ...32 w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 132: ...132 802 1X w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 310: ...310 Configuration Replace and Rollback w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 330: ...330 Dynamic Host Configuration Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 402: ...402 High Availability w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 462: ...462 Interfaces w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 482: ...482 IPv4 Addressing w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 506: ...506 IPv6 Addressing w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 582: ...582 Layer 2 w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 642: ...642 Multicast Source Discovery Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 662: ...662 Multiple Spanning Tree Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 690: ...690 Object Tracking w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 754: ...754 PIM Dense Mode w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 784: ...784 PIM Source Specific Mode w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 800: ...800 Power over Ethernet w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 876: ...876 Quality of Service w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 892: ...892 Routing Information Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1006: ...1006 Simple Network Management Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1018: ...1018 SONET SDH w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1048: ...1048 Broadcast Storm Control w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1096: ...1096 Uplink Failure Detection UFD w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1098: ...1098 Upgrade Procedures w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1196: ...1196 C Series Debugging and Diagnostics w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1252: ...1252 Standards Compliance w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1262: ...1262 Index w w w d e l l c o m s u p p o r t d e l l c o m ...