Chapter 5
Setup and Configuration
RUGGEDCOM ROX II
User Guide
796
Configuring IPv6 Neighbor Discovery
1
2
3
4
5
6
7
8
9
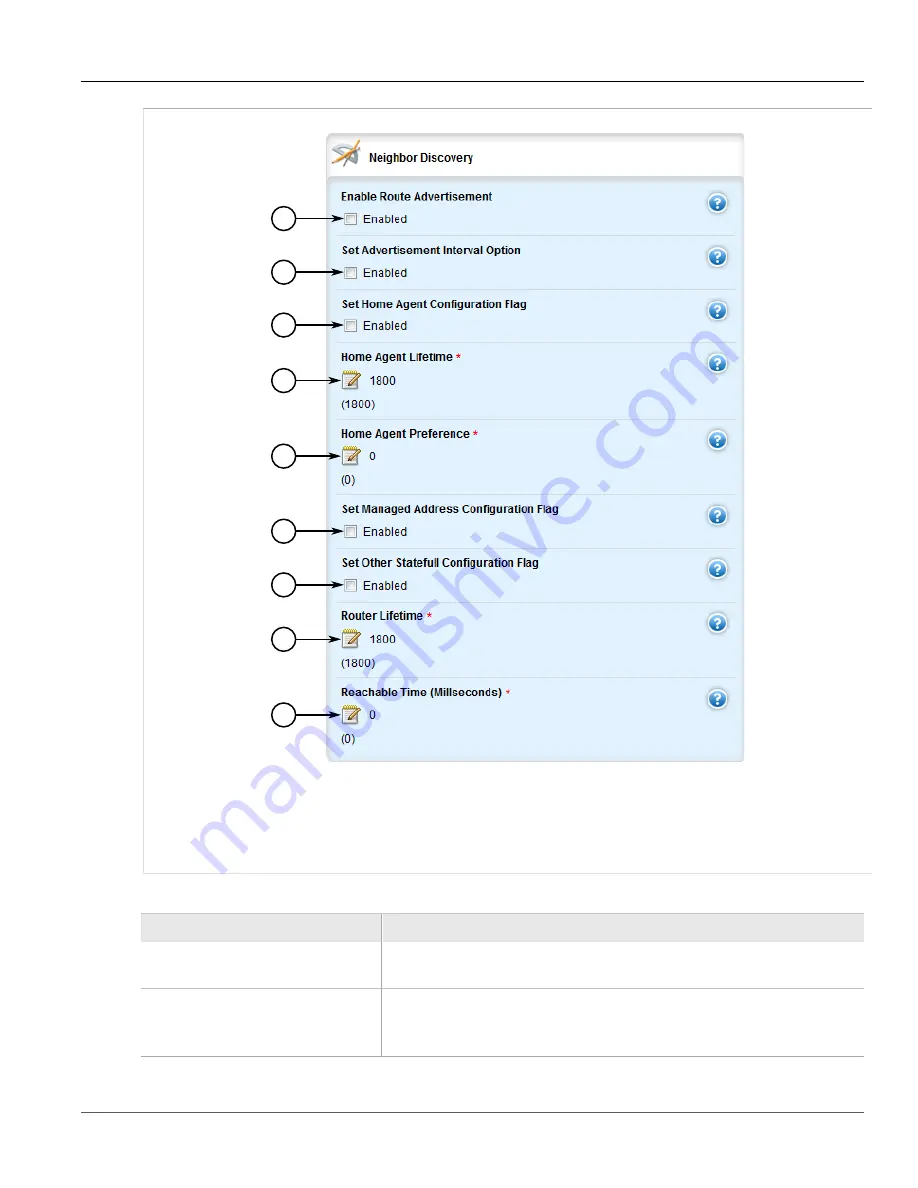
Figure 917: Neighbor Discovery Form
1.
Enable Route Advertisement Check Box
2.
Set Advertisement Interval Option Check Box
3.
Set Home Agent Configuration Flag
Check Box
4.
Home Agent Lifetime Box
5.
Home Agent Preference Box
6.
Set Managed Address Configuration Flag Check
Box
7.
Set Other Statefull Configuration Flag Check Box
8.
Router Lifetime Box
9.
Reachable Time Box
3. On the
Router Advertisement Interval
form, configure the following parameter(s) as required:
Parameter
Description
Interval
The interval value.
Prerequisite:
The value cannot be specified unless the unit is also specified.
Unit
Synopsis:
sec, msec
The interval unit.
Prerequisite:
The unit cannot be specified unless the value is also specified.
Содержание RUGGEDCOM RX1510
Страница 32: ...RUGGEDCOM ROX II User Guide Preface Customer Support xxxii ...
Страница 44: ...RUGGEDCOM ROX II User Guide Chapter 1 Introduction User Permissions 12 ...
Страница 62: ...RUGGEDCOM ROX II User Guide Chapter 2 Using ROX II Using the Command Line Interface 30 ...
Страница 268: ...RUGGEDCOM ROX II User Guide Chapter 4 System Administration Deleting a Scheduled Job 236 ...
Страница 852: ...RUGGEDCOM ROX II User Guide Chapter 5 Setup and Configuration Enabling Disabling an LDP Interface 820 ...






























