Chapter 5
Setup and Configuration
RUGGEDCOM ROX II
User Guide
586
Adding a VRRP Tracker
1
2
5
6
7
3
4
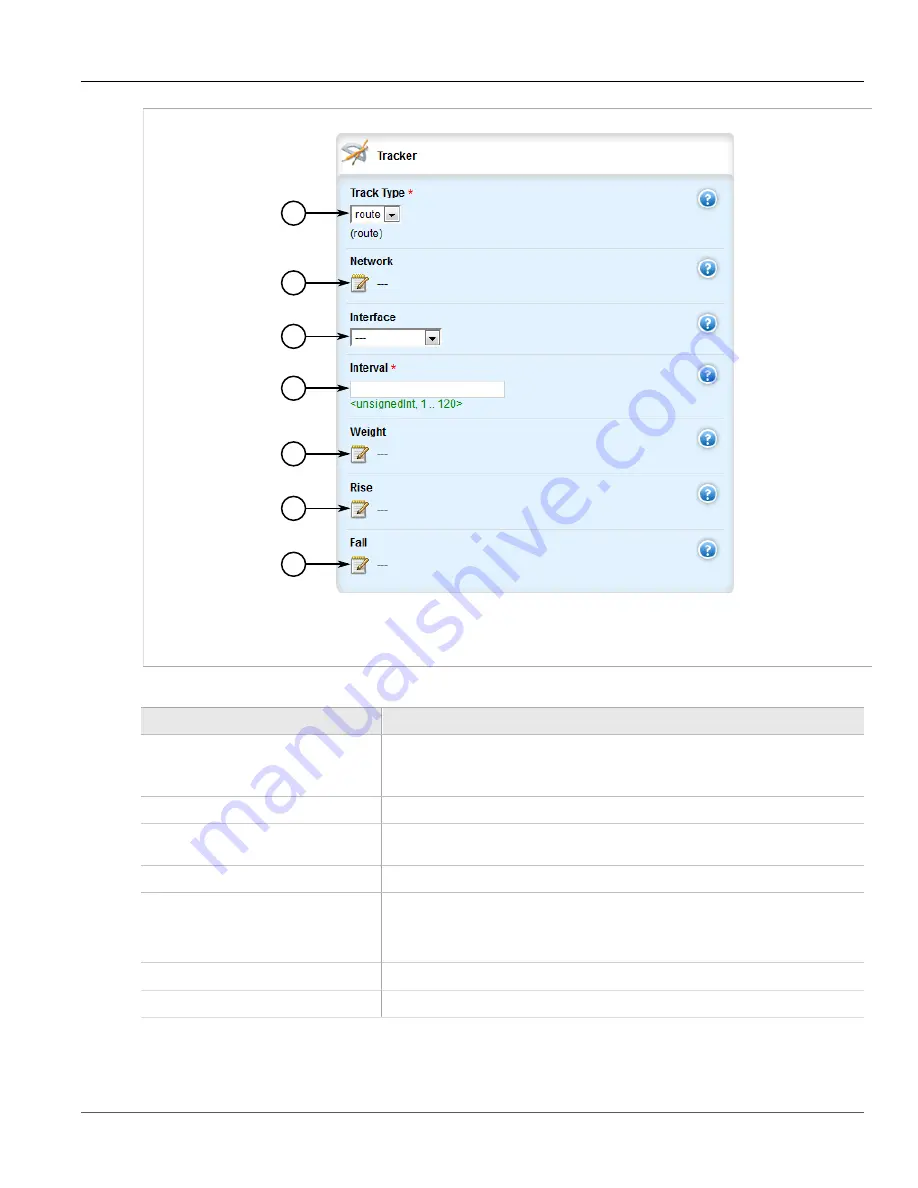
Figure 680: Tracker Form
1.
Tracker Type List
2.
Network Box
3.
Interface List
4.
Interval List
5.
Weight Box
6.
Rise Box
7.
Fall Box
5. Configure the following parameter(s) as required:
Parameter
Description
Track Type
Synopsis:
route
Default:
route
The type of condition for the tracker to check.
Network
The network to track. The tracker checks for a route to this network in the routing table.
Interface
The interface to the tracked network. The tracker rises only when the route to the
monitored network is through this interface.
Interval
The number of seconds between tracker queries.
Weight
The amount by which to increase or decrease the router's priority. When negative, the
priority decreases by this amount when the tracker falls. When positive, the priority
increases by this amount when the tracker rises. When not set, the state changes to the
fault state when the tracker falls.
Rise
The number of successful tracker queries before changing the router priority.
Fall
The number of unsuccessful tracker queries before changing the router priority.
6. Click
Commit
to save the changes or click
Revert All
to abort. A confirmation dialog box appears. Click
OK
to proceed.
Содержание RUGGEDCOM RX1510
Страница 32: ...RUGGEDCOM ROX II User Guide Preface Customer Support xxxii ...
Страница 44: ...RUGGEDCOM ROX II User Guide Chapter 1 Introduction User Permissions 12 ...
Страница 62: ...RUGGEDCOM ROX II User Guide Chapter 2 Using ROX II Using the Command Line Interface 30 ...
Страница 268: ...RUGGEDCOM ROX II User Guide Chapter 4 System Administration Deleting a Scheduled Job 236 ...
Страница 852: ...RUGGEDCOM ROX II User Guide Chapter 5 Setup and Configuration Enabling Disabling an LDP Interface 820 ...






























