Switch Security
This chapter describes the security mechanisms available to the switch. This chapter describes the following
security configuration activities:
•
Displaying the Main Security Interface
•
Access Point Detection
•
Wireless Intrusion Detection / Protection
•
Configuring Firewalls and Access Control Lists
•
Configuring NAT Information
•
Configuring IKE Settings
•
Configuring IPSec VPN
•
Configuring the Radius Server
•
Creating Server Certificates
•
Configuring Enhanced Beacons and Probes
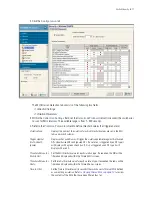
6.1 Displaying the Main Security Interface
Refer to main
Security
interface for a high level overview of device intrusion and switch access permission
options.
NOTE:
When the switch’s configuration is successfully updated (using the Web UI), the
effected screen is closed without informing the user their change was successful.
However, if an error were to occur, the error displays within the effected screen’s Status
field remains displayed. In the case of file transfer operations, the transfer screen remains
open during the transfer operation and remains open upon completion (with status
displayed within the Status field).
Summary of Contents for RFS Series
Page 1: ...M Motorola RFS Series Wireless LAN Switches WiNG System Reference Guide ...
Page 10: ...TOC 8 Motorola RF Switch System Reference Guide ...
Page 56: ...2 8 Motorola RF Switch System Reference ...
Page 334: ...5 52 Motorola RF Switch System Reference 2 Select the MU Status tab ...
Page 510: ...7 32 Motorola RF Switch System Reference Guide ...
Page 534: ...8 24 Motorola RF Switch System Reference Guide ...
Page 570: ...C 14 Motorola RF Switch System Reference Guide ...
Page 589: ......