client is blacklisted for a configurable timeout period known as the
known-client-
ageout
.
The
known-client-ageout
determines the time period in minutes for which a client device
is blacklisted. If after the timeout elapses, the client device MAC is configured on the RADIUS
server, MAC validation succeeds and the client device is granted wireless access.
Procedure
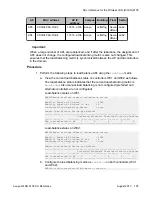
1. Enter wireless security configuration mode of the ACLI.
WC8180#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WCP8180(config)#wireless
WC8180(config-wireless)#security
2. Configure the
known-client-ageout
for example, for 30 minutes.
WC8180(config-security)#radius known-client-ageout 30
Note:
The default value is 30 minutes and the range is 1 to 65535 minutes.
3. View the
known-client-ageout
configuration.
WC8180(config-security)#show wireless security radius
Radius server timeout: 2 (sec.)
Radius server retries: 3
Radius known client db ageout: 30 (min.)
Configuring a trap for authentication failure
Use the following procedure to configure a trap for authentication failure.
This trap is useful to detect the problem when MAC validation against a RADIUS server
fails.
Procedure
1. Enter the configuration mode of the ACLI.
WC8180#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WCP8180(config)#
2. Enable the authentication-failure trap.
WC8180(config)#snmp-server notification-control
avWlanClientAuthenticationFail
Note:
To view a complete list of snmp-server notification types and their status, execute
the command
show snmp-server notification-control
.
ACLI reference for Wireless LAN (WLAN) 8100
118 Avaya WLAN 8100 CLI Reference
August 2013