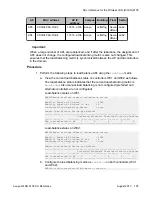
5. Verify threat mitigation configuration using the following command.
Show wireless security wids-wips mitigation
Sample Output:
WCP8180#show wireless security wids-wips mitigation
ap-threat-mitigation: enabled
client-threat-mitigation: disabled
6. Verify AP deauthentication attacks using the following command.
Show wireless security wids-wips ap-deauth-attacks
Sample Output:
WCP8180#show wireless security wids-wips ap-deauth-attacks
Target BSSID Channel Classify Since Last RFScan
----------------- ---------- -------------------- ------------
5C:E2:86:0F:F7:70 3 2:02:57:19 0d:00:00:00
70:38:EE:89:C4:10 11 1:18:33:49 0d:00:09:37
5C:E2:86:0F:F2:10 10 1:18:33:19 0d:00:00:07
70:38:EE:89:C3:F0 11 1:18:27:48 0d:00:00:07
00:1B:4F:6A:59:B0 11 1:03:01:11 0d:00:00:07
00:1B:4F:6A:64:F0 6 0d:22:57:41 0d:22:57:41
7. Verify Ageout configuration using the following command.
Show wireless security wids-wips ageout
Sample Output:
WCP8180#show wireless security wids-wips ageout
adhoc-clients :1440 minutes
ap-failure :1440 minutes
detected-client :300 minutes
rf-scan :1440 minutes
Configuring a MAC filter blacklist
Use this procedure to configure a MAC filter blacklist.
In prior releases of the WLAN 8100, to filter out a client MAC, you would need to add it the
Blacklist database and enable MAC validation on the network profile. This also required all
valid clients to be added to the Whitelist database. From release 2.1 onwards, you can blacklist
a client MAC independent of a Whitelist or RADIUS based MAC validation, by configuring the
client in a MAC filter blacklist.
Procedure
1. Enter wireless security configuration mode of the CLI.
WCP8180#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WCP8180(config)#wireless
WCP8180(config-wireless)#security
ACLI reference for Wireless LAN (WLAN) 8100
110 Avaya WLAN 8100 CLI Reference
August 2013