File Anti-Virus
81
The file scanning mode determines the File Anti-Virus processing conditions.
You have following options:
Smart mode
. This mode is aimed at speeding up file processing and
return them to the user. When it is selected, a decision to scan is made
based on analyzing the operations performed with the file.
For example, when using a Microsoft Office file, Kaspersky Anti-Virus
scans the file when it is first opened and last closed. All operations in
between that overwrite the file are not scanned.
Smart mode is the default.
On access and modification
– File Anti-Virus scans files as they are
opened or edited.
On access
– only scans files when an attempt is made to open them.
On execution
– only scans files when an attempt is made to run them.
You might need to pause File Anti-Virus when performing tasks that require sig-
nificant operating system resources. To lower the load and ensure that the user
regains access to files quickly, we recommend configuring the component to
disable at a certain time or while certain programs are used.
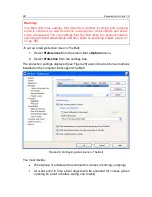
To pause the component for a certain length of time, check
On schedule
and
in the window that opens (see Figure 20) click
Schedule
to assign a time frame
for disabling and resuming the component. To do so, enter a value in the format
HH:MM in the corresponding fields.
Figure 21. Pausing the component
To disable the component when working with programs that require significant
resources, check
On applications startup
and edit the list of programs in the
window that opens (see Figure 22) by clicking
List
.
To add an application to the list, use the
Add
button. A context menu will open,
and by clicking
Browse
you can go to the standard file selection window and
specify the executable file the application to add. Or, go to the list of applications
currently running from the
Applications
item and select the one you want.
To delete an application, select it from a list and click
Delete
.