Protection management system
67
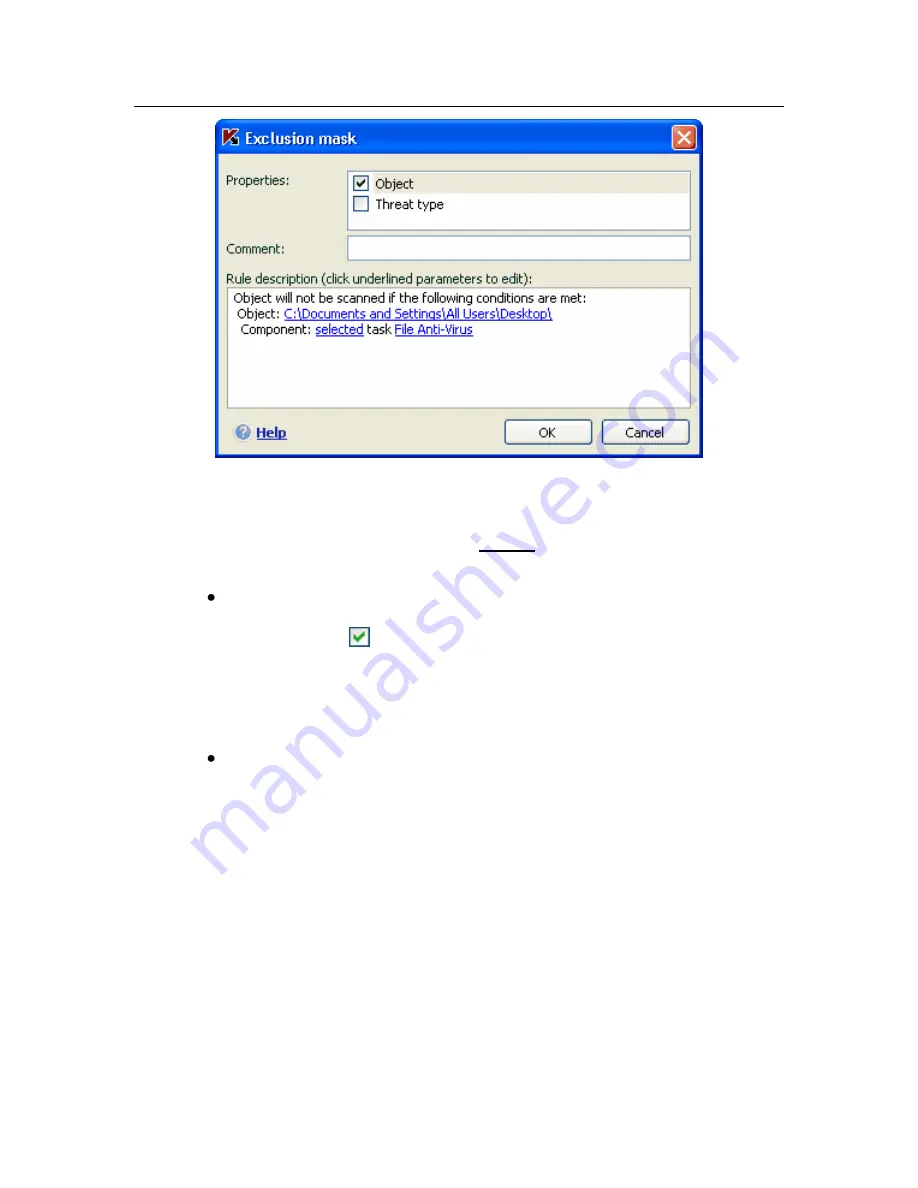
Figure 12. Creating an exclusion rule
3. Assign values to the selected exclusion types. To do so, left-click in the
Rule description
section on the specify link located next to the exclu-
sion type:
For the
Object
type, enter its name in the window that opens (this
can be a file, a particular folder, or a file mask (see A.2 on pg.
216). Check
Include subfolders
for the object (file, file mask,
folder) to be recursively excluded from the scan. For example, if
you assign
C:\Program Files\winword.exe
as an exclusion and
checked the subfolder option, the file
winword.exe
will be excluded
from the scan if found in any
C:\Program Files
subfolders.
Enter the full name of the threat that you want to exclude from
scans as given in the Virus Encyclopedia or use a mask (see A.3
on pg. 216) for the
Threat type
.
For some threat type, you can assign advanced conditions for ap-
plying rules in the
Advanced settings
field. In most cases, this
field is filled in automatically when you add an exclusion rule from a
Proactive Defense notification.
You can add advanced settings for the following threats, among
others:
o
Invader (injects into program processes). For this threat, you
can give a name, mask, or complete path to the object being
injected into (for example, a .dll file) as an additional exclusion
condition.






























