Troubleshooting
Page 140
FortiRecorder 2.4.2 Administration Guide
http://www.wireshark.org/
).
For example, you could use PuTTY or Microsoft HyperTerminal to save the sniffer output to a
file. Methods may vary. See the documentation for your CLI client.
Requirements
• terminal emulation software such as
• a plain text editor such as Notepad
• a
• network protocol analyzer software such as
To view packet capture output using PuTTY and Wireshark
1.
On your management computer, start PuTTY.
2.
Use PuTTY to connect to the FortiRecorder appliance using either a local console, SSH, or
Telnet connection.
3.
Type the packet capture command, such as:
diag sniffer packet port1 'src host 10.0.0.1 and tcp port 443' 3
but do
not
press Enter yet.
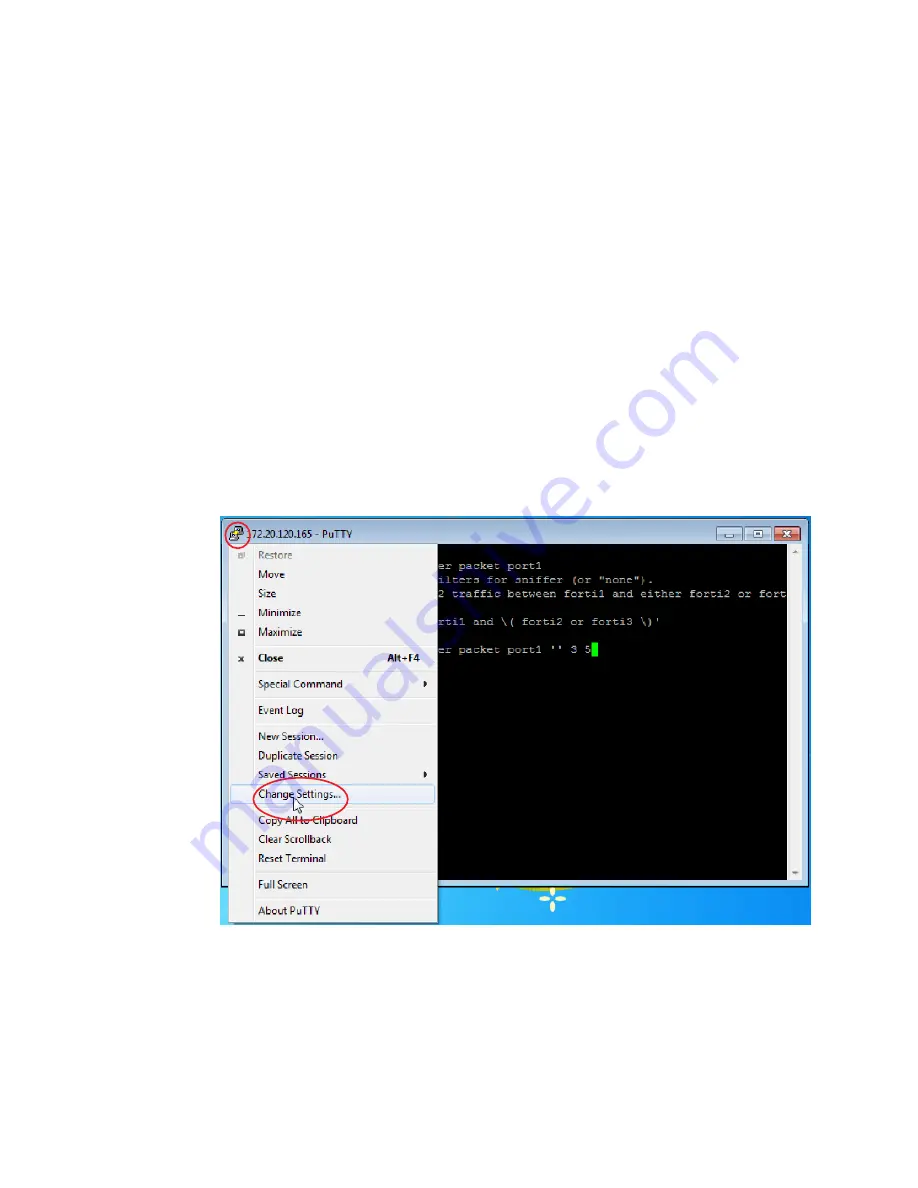
4.
In the upper left corner of the window, click the PuTTY icon to open its drop-down menu,
then select
Change Settings
.
A dialog appears where you can configure PuTTY to save output to a plain text file.
5.
In the
Category
tree on the left, go to
Session > Logging.
6.
In
Session logging
, select
Printable output
.
7.
In
Log file name
, click the
Browse
button, then choose a directory path and file name such
as
C:\Users\MyAccount\packet_capture.txt
to save the packet capture to a plain
text file. (You do not need to save it with the
.log
file extension.)
8.
Click
Apply
.






























