Alert System Components
367
There are various types of alert that may be created within the system.
These are detailed in
“Alerts”
on
page 325
.
Each alert type may be configured with suitable parameters for its type.
For example, a
Sound
alert only requires the name of a suitable audio file,
whereas an
alert requires details of the SMTP host to use, along
with details of the source and destination e-mail addresses and the
subject and contents of the message.
Other than the
Sound
alert type, which requires only the name of a
suitable audio file, the configuration of an alert allows you to enter
tokens in the fields used to generate the alert. When the alert is
generated these tokens are replaced by the values they represent. This
allows you to configure dynamic alert messages.
The
Alerts System
supports the following tokens:
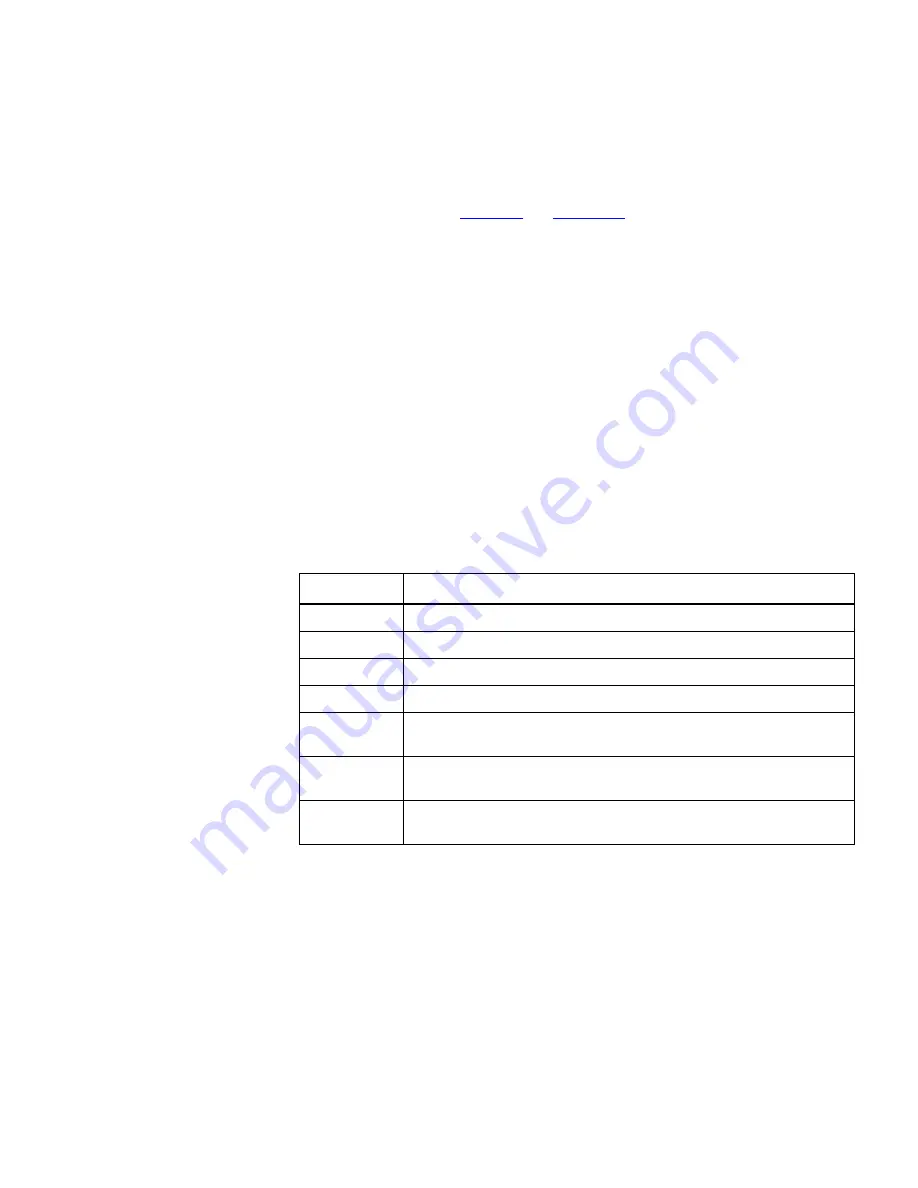
Table 61
Alert System Tokens
To insert a token into a field, place the cursor at the location where the
token is to be inserted and select the token from the table of tokens
shown on the
Add Alerts
dialog box. Tokens may also be typed in directly.
For example, the sample
Pop-up
alert that is provided with the system is
defined as follows:
Token
Replaced In Generated Alert By
$date$
The date when the event was generated.
$time$
The time when the event was generated.
$device$
The name of the item that the event was generated for.
$ipAddr$
The IP address of the item that the event was generated for.
$event
Severity$
The severity of the generated event.
$event
Description$
The description of the generated event.
$event
Explanation$
An explanation of the event, including possible causes and
resolutions.
Summary of Contents for 3C15500 - Network Director - PC
Page 4: ......
Page 34: ......
Page 38: ...34 ABOUT THIS GUIDE ...
Page 50: ...46 CHAPTER 1 GETTING STARTED ...
Page 64: ...60 CHAPTER 2 PRODUCT ACTIVATION ...
Page 213: ...Components 209 Figure 75 Export to Visio Dialog Box ...
Page 220: ...216 CHAPTER 5 WORKING WITH THE MAP Figure 84 Double Clicking on a Router in the Tree ...
Page 264: ...260 CHAPTER 6 VIEWING DEVICE DETAILS Figure 117 Security Tab for a Device ...
Page 276: ...272 CHAPTER 6 VIEWING DEVICE DETAILS ...
Page 322: ...318 CHAPTER 7 MONITORING THE NETWORK ...
Page 385: ...Examples 381 Figure 189 Attach Alerts Dialog Box ...
Page 406: ...402 CHAPTER 9 PERFORMANCE REPORTING ...
Page 431: ...Components 427 History View dialog box Figure 210 History View Dialog Box ...
Page 440: ...436 CHAPTER 10 RMON Host View dialog box Figure 219 Host View Dialog Box ...
Page 476: ...472 CHAPTER 11 CREATING REPORTS ...
Page 502: ...498 CHAPTER 12 CONFIGURING SINGLE DEVICES ...
Page 526: ...522 CHAPTER 13 VLAN MANAGEMENT Figure 272 Options Dialog Box VLANs Tab ...
Page 567: ...Components 563 Figure 305 Selecting the Link to the End Station on the Map ...
Page 626: ...622 CHAPTER 14 BULK CONFIGURATION ...
Page 684: ...680 CHAPTER 16 UPGRADING DEVICE SOFTWARE ...
Page 814: ...810 CHAPTER 19 BACKING UP DEVICE CONFIGURATIONS ...
Page 838: ...834 CHAPTER 20 LIVE UPDATE ...
Page 894: ...890 APPENDIX G ADDING MAC ADDRESS VENDOR TRANSLATIONS ...
















































