597
On the called side
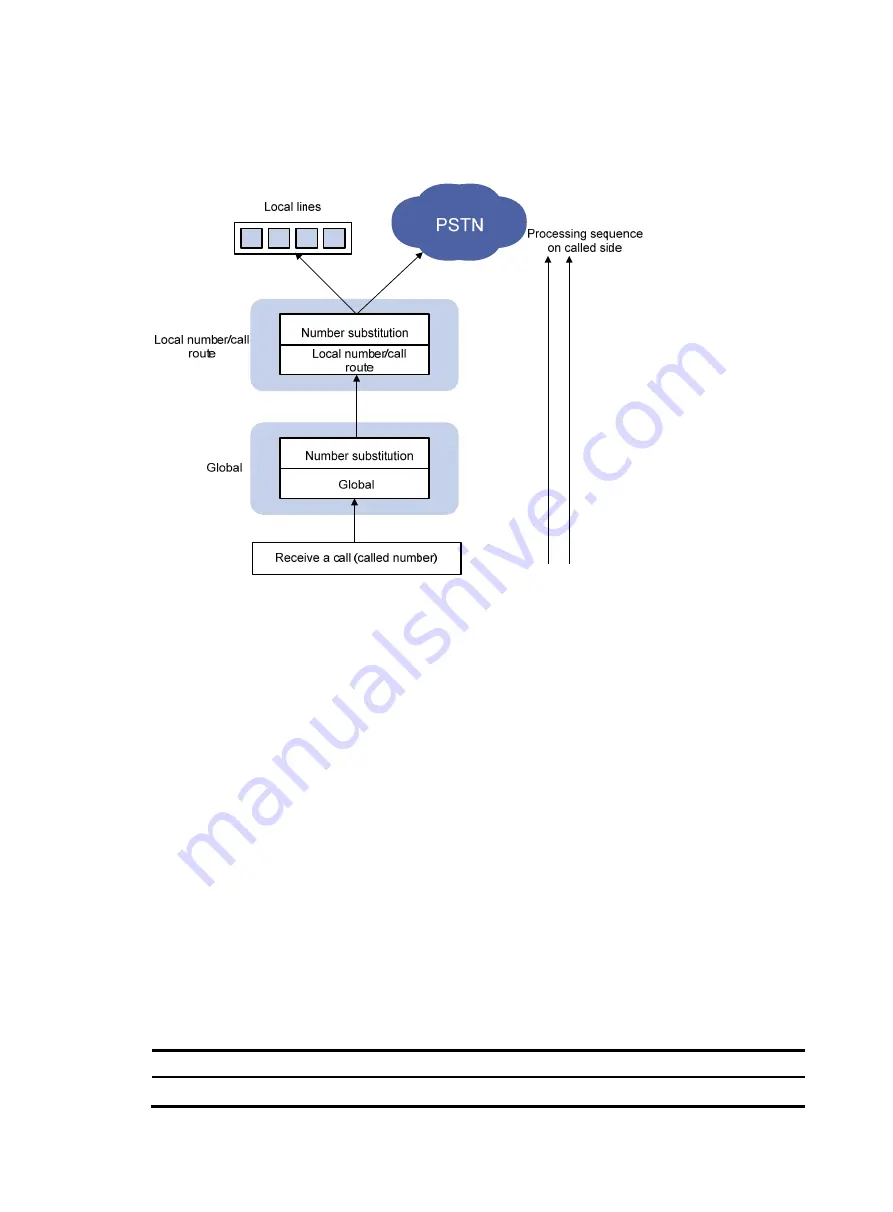
shows the dial plan operation process on the called side.
Figure 616
Flow chart for dial plan operation process on the called side
1.
After receiving a voice call (the called number), the voice gateway on the called side performs
global calling/called number substitution.
2.
The voice gateway on the called side selects proper local numbers or call routes based on the local
number or call route selection priority rules. Number substitution might also be involved during the
local number or call route selection. If the called party is a local number, the gateway directly
connects the line. If the called party is a PSTN subscriber, the gateway initiates a call and sends the
calling and called numbers to the PSTN. The PBX in the PSTN connects the call.
Regular expression
You will use some regular expressions frequently when you configure number substitution rules. Regular
expressions are a powerful and flexible tool for pattern matching and substitution. They are not restricted
to a language or system, and have been widely accepted.
When using a regular expression, you must construct a matching pattern according to certain rules, and
then compare the matching pattern with the target object. The simplest regular expressions do not
contain any meta-character. For example, you can specify a regular expression
hello
, which only
matches the string
hello
.
To help you construct matching patterns flexibly, regular expressions support some special characters,
called meta-characters, which define the way other characters appear in the target object.
Table 231
Meta-characters
Meta-character Meaning
0-9
Digits 0 through 9.
Содержание MSR SERIES
Страница 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Страница 20: ...3 Figure 3 Initial page of the Web interface ...
Страница 42: ...25 Figure 13 Firefox Web browser setting ...
Страница 59: ...42 Figure 27 Checking the basic service configuration ...
Страница 73: ...56 Figure 35 Sample interface statistics ...
Страница 156: ...139 Figure 139 Rebooting the 3G modem ...
Страница 168: ...151 Figure 152 Configuring Web server 2 ...
Страница 174: ...157 Figure 158 Configure the URL filtering function ...
Страница 187: ...170 Upon detecting the Land or Smurf attack on Ethernet 0 2 Router outputs an alarm log and drops the attack packet ...
Страница 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Страница 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Страница 255: ...238 Figure 241 Advanced limit setting ...
Страница 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Страница 354: ...337 Figure 339 Configuring a login control rule so Host B cannot access Router through the Web ...
Страница 400: ...383 Figure 387 Verifying the configuration ...
Страница 405: ...388 ...
Страница 523: ...506 Figure 530 Ping configuration page ...
Страница 538: ...521 a Click Device A on the topology diagram b Click Ethernet 0 2 on the panel diagram c Click Port Guard ...
Страница 744: ...727 Verifying the configuration In the case that the IP network is unavailable calls can be made over PSTN ...
Страница 775: ...758 Figure 785 Configuring a jump node ...
Страница 791: ...774 Figure 801 Configuring a jump node ...