226
Configuring ACLs
The Web interface provides the following ACL configuration functions:
•
Configuring an IPv4 ACL
•
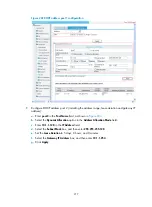
Configuring a rule for a basic IPv4 ACL
•
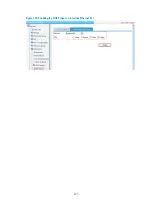
Configuring a rule for an advanced IPv4 ACL
•
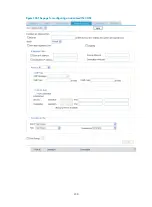
Configuring a rule for an Ethernet frame header ACL
Overview
An access control list (ACL) is a set of rules (or permit or deny statements) for identifying traffic based on
criteria such as source IP address, destination IP address, and port number.
ACLs are essentially used for packet filtering. A packet filter drops packets that match a deny rule and
permits packets that match a permit rule. ACLs are also widely used by many modules (for example, QoS
and IP routing) for traffic identification.
IPv4 ACLs include the following categories, as shown in
.
Table 110
IPv4 ACL categories
Category
ACL number
Match criteria
Basic ACLs
2000 to 2999
Source IPv4 address
Advanced ACLs 3000 to 3999
Source/destination IPv4 address, protocol number, and other Layer
3 and Layer 4 header fields
Ethernet frame
header ACLs
4000 to 4999
Layer 2 header fields, such as source and destination MAC
addresses, 802.1p priority, and link layer protocol type
For more information about IPv4 ACL, see
ACL and QoS Configuration Guide
in
HP MSR Router Series
Configuration Guides (V5)
.
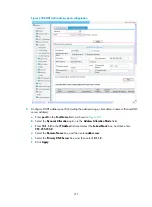
Recommended IPv4 ACL configuration procedure
Step
Remarks
1.
Required.
The category of the added ACL depends on the ACL
number that you specify.
2.
Configuring a rule for a basic IPv4 ACL
Required.
Complete one of these tasks according to the ACL
category.
3.
Configuring a rule for an advanced IPv4 ACL
4.
Configuring a rule for an Ethernet frame header
ACL
.
Содержание MSR SERIES
Страница 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Страница 20: ...3 Figure 3 Initial page of the Web interface ...
Страница 42: ...25 Figure 13 Firefox Web browser setting ...
Страница 59: ...42 Figure 27 Checking the basic service configuration ...
Страница 73: ...56 Figure 35 Sample interface statistics ...
Страница 156: ...139 Figure 139 Rebooting the 3G modem ...
Страница 168: ...151 Figure 152 Configuring Web server 2 ...
Страница 174: ...157 Figure 158 Configure the URL filtering function ...
Страница 187: ...170 Upon detecting the Land or Smurf attack on Ethernet 0 2 Router outputs an alarm log and drops the attack packet ...
Страница 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Страница 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Страница 255: ...238 Figure 241 Advanced limit setting ...
Страница 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Страница 354: ...337 Figure 339 Configuring a login control rule so Host B cannot access Router through the Web ...
Страница 400: ...383 Figure 387 Verifying the configuration ...
Страница 405: ...388 ...
Страница 523: ...506 Figure 530 Ping configuration page ...
Страница 538: ...521 a Click Device A on the topology diagram b Click Ethernet 0 2 on the panel diagram c Click Port Guard ...
Страница 744: ...727 Verifying the configuration In the case that the IP network is unavailable calls can be made over PSTN ...
Страница 775: ...758 Figure 785 Configuring a jump node ...
Страница 791: ...774 Figure 801 Configuring a jump node ...