421
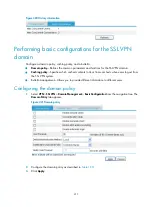
3.
Configure the security policy as describe in
4.
Click
Apply
.
Table 186
Configuration items
Item Description
Name
Enter a name for the security policy.
Level
Set a level for the security policy. A larger number means a higher level.
If multiple security policies are defined, the system first uses the security policy with the
highest priority to check the user host. If the host does not satisfy the security policy, the
system uses the security policy with the second highest priority, and so forth until the
host satisfies a security policy or fails security check. The resources that the user can
access are those defined in the security policy that the user first passes. Therefore, when
you configure security policies, specify more resources for a security policy that has a
higher level.
Description
Enter a description for the security policy.
Policy Configuration
Set check rules for the security policy.
Check rules fall into seven categories: operating system, browser, antivirus software,
firewall, certificate, file, and process.
To pass the check of a category, a host needs to satisfy at least one rule of the category.
To pass the check of a security policy, a host must satisfy all categories of the policy.
Click the expansion button before a category to view the rule information. Click the
Add
button to add a rule for the category. For more information about rule
configuration, see
Resource
Configuration
Specify the resources that can be accessed by user hosts that satisfy the security policy.
You can select
All Web Proxies
,
All TCP Applications
, and
all IP Networks
. To select
specific Web proxies, TCP applications, or IP networks, click the corresponding
expansion button.
Table 187
Configuration items
Item Description
Operating
System
Rule Name
Enter a name for the operating system rule.
Type
Specify the operating system type. A user host must run the specified type of
operating system to pass security check.
Version
Specify the operating system version. The operating system of a user host must
satisfy the version requirement to pass security check.
Patch
Specify the operating system patches. The operating system of a user host must
have the specified patches installed to pass security check.
Browser
Rule Name
Enter a name for the browser rule.
Type
Specify the browser type. A user host must use the specified type of browser to
pass security check.
Содержание MSR SERIES
Страница 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Страница 20: ...3 Figure 3 Initial page of the Web interface ...
Страница 42: ...25 Figure 13 Firefox Web browser setting ...
Страница 59: ...42 Figure 27 Checking the basic service configuration ...
Страница 73: ...56 Figure 35 Sample interface statistics ...
Страница 156: ...139 Figure 139 Rebooting the 3G modem ...
Страница 168: ...151 Figure 152 Configuring Web server 2 ...
Страница 174: ...157 Figure 158 Configure the URL filtering function ...
Страница 187: ...170 Upon detecting the Land or Smurf attack on Ethernet 0 2 Router outputs an alarm log and drops the attack packet ...
Страница 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Страница 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Страница 255: ...238 Figure 241 Advanced limit setting ...
Страница 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Страница 354: ...337 Figure 339 Configuring a login control rule so Host B cannot access Router through the Web ...
Страница 400: ...383 Figure 387 Verifying the configuration ...
Страница 405: ...388 ...
Страница 523: ...506 Figure 530 Ping configuration page ...
Страница 538: ...521 a Click Device A on the topology diagram b Click Ethernet 0 2 on the panel diagram c Click Port Guard ...
Страница 744: ...727 Verifying the configuration In the case that the IP network is unavailable calls can be made over PSTN ...
Страница 775: ...758 Figure 785 Configuring a jump node ...
Страница 791: ...774 Figure 801 Configuring a jump node ...