Chapter 15 The Certificates Screens
User’s Guide
182
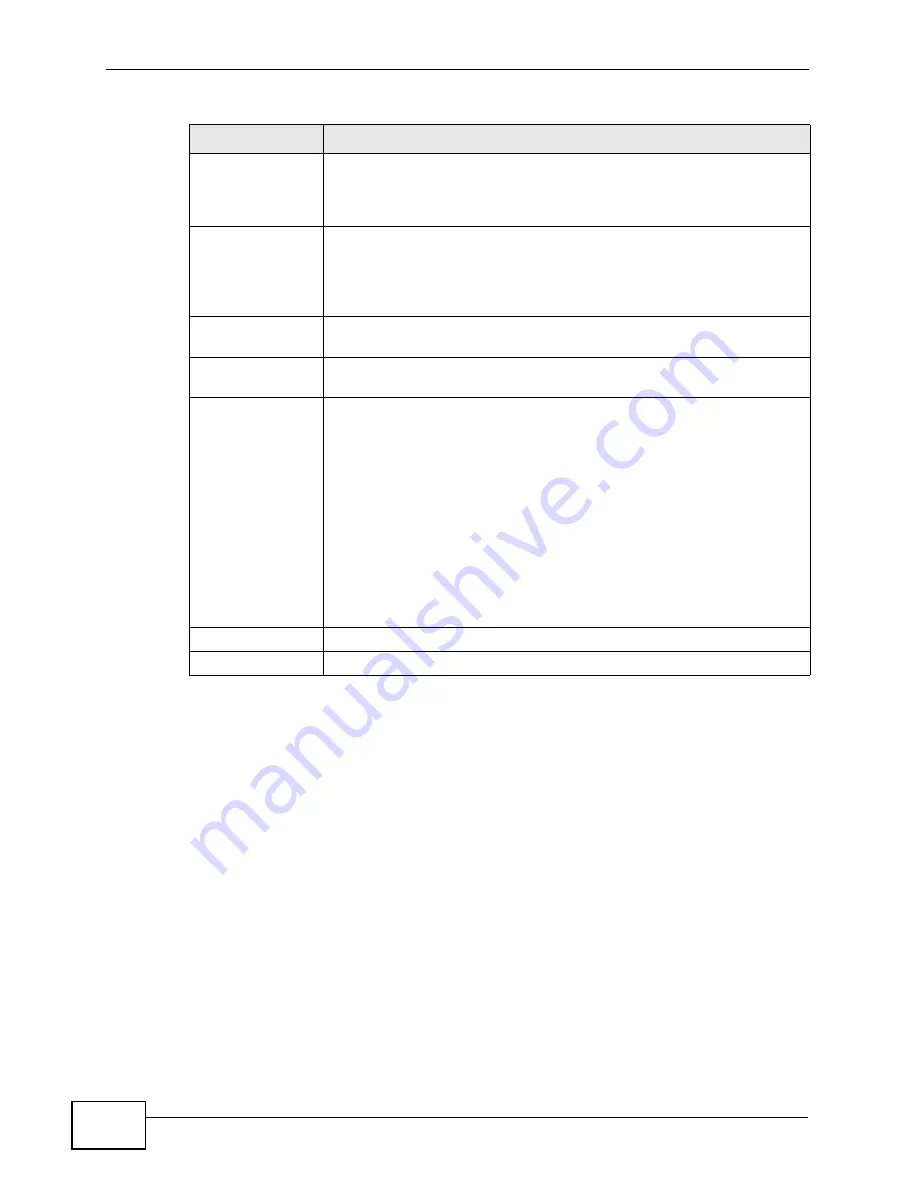
Key Usage
This field displays for what functions the certificate’s key can be used.
For example, “DigitalSignature” means that the key can be used to
sign certificates and “KeyEncipherment” means that the key can be
used to encrypt text.
Basic Constraint
This field displays general information about the certificate. For
example, Subject Type=CA means that this is a certification
authority’s certificate and “Path Length Constraint=1” means that
there can only be one certification authority in the certificate’s path.
This field does not display for a certification request.
MD5 Fingerprint
This is the certificate’s message digest that the WiMAX Modem
calculated using the MD5 algorithm.
SHA1 Fingerprint
This is the certificate’s message digest that the WiMAX Modem
calculated using the SHA1 algorithm.
Certificate in PEM
(Base-64)
Encoded Format
This read-only text box displays the certificate or certification request
in Privacy Enhanced Mail (PEM) format. PEM uses lowercase letters,
uppercase letters and numerals to convert the binary certificate into a
printable form.
You can copy and paste a certification request into a certification
authority’s web page, an e-mail that you send to the certification
authority or a text editor and save the file on a management
computer for later manual enrollment.
You can copy and paste a certificate into an e-mail to send to friends
or colleagues or you can copy and paste a certificate into a text editor
and save the file on a management computer for later distribution
(via floppy disk for example).
Apply
Click to save your changes.
Cancel
Click to return to the previous screen without saving your changes.
Table 64
TOOLS > Certificates > Trusted CAs > Edit (continued)
LABEL
DESCRIPTION
Summary of Contents for MAX-306M1
Page 2: ......
Page 8: ...Safety Warnings User s Guide 8...
Page 10: ...Contents Overview User s Guide 10...
Page 24: ...List of Figures User s Guide 24...
Page 30: ...30...
Page 63: ...63 PART II Basic Screens The Main Screen 38 The Setup Screens 65...
Page 64: ...64...
Page 72: ...72...
Page 84: ...Chapter 7 The LAN Configuration Screens User s Guide 84...
Page 96: ...Chapter 8 The WAN Configuration Screens User s Guide 96...
Page 108: ...Chapter 9 The VPN Transport Screens User s Guide 108...
Page 118: ...Chapter 10 The NAT Configuration Screens User s Guide 118...
Page 130: ...130...
Page 148: ...Chapter 12 The Service Configuration Screens User s Guide 148...
Page 158: ...Chapter 13 The Phone Screens User s Guide 158...
Page 164: ...Chapter 14 The Phone Book Screens User s Guide 164...
Page 166: ...166...
Page 188: ...Chapter 15 The Certificates Screens User s Guide 188...
Page 198: ...Chapter 16 The Firewall Screens User s Guide 198...
Page 218: ...Chapter 19 QoS User s Guide 218...
Page 234: ...Chapter 20 The Logs Screens User s Guide 234...
Page 247: ...247 PART VI Troubleshooting and Specifications Troubleshooting 249 Product Specifications 257...
Page 248: ...248...
Page 256: ...Chapter 22 Troubleshooting User s Guide 256...
Page 264: ...Chapter 23 Product Specifications User s Guide 264...
Page 266: ...266...
Page 298: ...Appendix B Setting Up Your Computer s IP Address User s Guide 298...
Page 308: ...Appendix C Pop up Windows JavaScripts and Java Permissions User s Guide 308...
Page 352: ...Appendix E Importing Certificates User s Guide 352...
Page 354: ...Appendix F SIP Passthrough User s Guide 354...
Page 370: ...Appendix I Customer Support User s Guide 370...
Page 376: ...Index User s Guide 376...
















































