Relevant Logs
None.
10.2.2 The Gateway Address Is Maliciously Changed
Common Causes
This fault is commonly caused by one of the following:
l
An attacker sends bogus gratuitous ARP packets to users. Users change their gateway
address after receiving the gratuitous ARP packets.
l
An attacker sends bogus ICMP unreachable packets or ICMP redirect packets to users.
Troubleshooting Flowchart
An attacker sends gratuitous ARP packets with the source IP address being the IP address of the
gateway on the LAN. After receiving the gratuitous ARP packets, hosts on the LAN change
their gateway MAC address to the MAC address of the attacker. As a result, the hosts cannot
access the network.
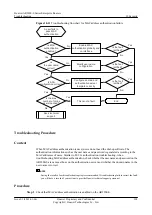
shows the troubleshooting flowchart.
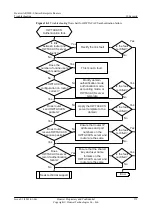
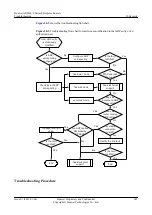
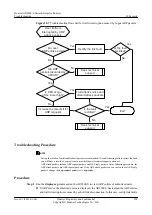
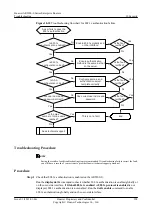
Figure 10-6
Troubleshooting flowchart for gateway address spoofing
The gateway
address is
maliciously changed
Are gateway
anti-collision entries
generated?
No
Configure a policy to
discard attack packets
Is the fault
rectified?
Is the fault
rectified?
Yes
No
No
Yes
Seek technical support
No
End
Is ARP
gateway anti-collision
configured?
Yes
No
Configure gateway anti-
collision
Is the fault
rectified?
Yes
No
Does the
router function as the
gateway?
Yes
Configure the router as
the gateway
Yes
Huawei AR2200-S Series Enterprise Routers
Troubleshooting
10 Security
Issue 01 (2012-01-06)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
287