AP-51xx Access Point Product Reference Guide
3-12
a. Enter the
Extended Services Set Identification (ESSID)
and name
associated with the
WLAN. For additional information on creating and editing up to 16 WLANs per access
point, see
Creating/Editing Individual WLANs on page 5-30
.
b. Use the
Available On
checkboxes to define whether the target WLAN is operating over
the 802.11a or 802.11b/g radio. Ensure the radio selected has been enabled (see step 8).
c. Even an access point configured with minimal values must protect its data against theft
and corruption. A security policy should be configured for WLAN1 as part of the basic
configuration outlined in this guide. A security policy can be configured for the WLAN
from within the
Quick Setup
screen. Policies can be defined over time and saved to be
used as needed as security requirements change. Motorola recommends you familiarize
yourself with the security options available on the access point before defining a
security policy. Refer to
Configuring WLAN Security Settings on page 3-12
.
10. Click
Apply
to save any changes to the access point Quick Setup screen. Navigating away
from the screen without clicking Apply results in all changes to the screens being lost.
11. Click
Undo Changes
(if necessary) to undo any changes made. Undo Changes reverts the
settings displayed on the access point Quick Setup screen to the last saved configuration.
3.5.1.1 Configuring WLAN Security Settings
To configure a basic security policy for a WLAN:
1.
From the access point Quick Setup screen, click the
Create
button to the right of the Security
Policy item.
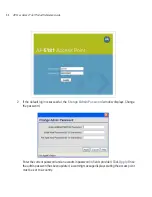
The
New Security Policy
screen displays with the
Manually Pre-shared key/No
authentication
and
No Encryption
options selected. Naming and saving such a policy (as
is) would provide no security and might only make sense in a guest network wherein no
sensitive data is either transmitted or received. Consequently, at a minimum, a basic
security scheme (in this case WEP 128) is recommended in a network environment wherein
sensitive data is transmitted.
2.
Ensure the
Name
of the security policy entered suits the intended configuration or function
of the policy.
Multiple WLANs can share the same security policy, so be careful not to name security
policies after specific WLANs or risk defining a WLAN to single policy. Motorola
NOTE
For information on configuring the other encryption and authentication
options available to the access point, see
Configuring Security Options on
page 6-2
.
Summary of Contents for AP 5131 - Wireless Access Point
Page 1: ...AP 51xx Access Point Product Reference Guide ...
Page 3: ...AP 51xx Access Point Product Reference Guide 72E 103901 01 January 2008 ...
Page 4: ......
Page 44: ...AP 51xx Access Point Product Reference Guide 1 28 ...
Page 76: ...AP 51xx Access Point Product Reference Guide 2 32 ...
Page 92: ...AP 51xx Access Point Product Reference Guide 3 16 ...
Page 588: ...AP 51xx Access Point Product Reference Guide 8 254 ...
Page 610: ...AP 51xx Access Point Product Reference Guide 9 22 3 Define a mesh supported WLAN ...
Page 623: ...Configuring Mesh Networking 9 35 3 Determine the Radio MAC Address and BSSID MAC Addresses ...
Page 653: ...Adaptive AP 10 25 line con 0 line vty 0 24 end ...
Page 654: ...AP 51xx Access Point Product Reference Guide 10 26 ...
Page 666: ...AP 51xx Access Point Product Reference Guide A 12 ...
Page 690: ...AP 51xx Access Point Product Reference Guide C 4 ...
Page 696: ...AP 51xx Access Point Product Reference Guide IN 10 ...
Page 697: ......