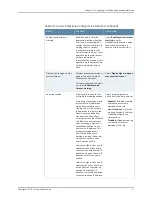
Table 12: User Role Terminal Services Configuration Details
(continued)
Your Action
Function
Option
Terminal Services > Terminal Services Sessions > Type > Windows Terminal Services >
Start Application
Select the
Launch Seamless
Window
check box to enable
this feature.
Allows you to have the
Windows application server
manage the display of the
application.
Launch Seamless Window
Specify the path.
Specifies where the
application’s executable file
resides on the terminal server
in the Path to application box
(visible only when you clear
Launch seamless window
).
Path to application
Specify the directory.
Specifies where the terminal
server should place working
files for the application in the
Working directory box.
Working directory
Terminal Services > Terminal Services Sessions > Type > Windows Terminal Services >
Connect Devices tab
Select the
Connect drives
check box to enable this
feature.
Allows you to connect the
user’s local drive to the
terminal server, enabling the
user to copy information from
the terminal server to his local
client directories.
Connect drives
Select the
Connect printers
check box to enable this
feature.
Allows you to connect the
user’s local printers to the
terminal server, enabling the
user to print information from
the terminal server to his local
printer.
Connect printers
Select the
Connect COM Ports
check box to enable this
feature.
Allows you to connect the
user’s COM ports to the
terminal server, allowing
communication between the
terminal server and the
devices on his serial ports.
Connect COM Ports
Select the
Allow Clibboart
Sharing
check box to enable
this feature.
Enables you to allow the
contents of the clipboard to be
shared between the user’s
host computer and the
terminal server.
Allow Clibboard Sharing
Select the
Connect smart
cards
check box to enable this
feature.
Enables you to allow users to
use smart cards to
authenticate their remote
desktop sessions.
Connect smart cards
Copyright © 2010, Juniper Networks, Inc.
54
Configuring Secure Access Devices Guide
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...