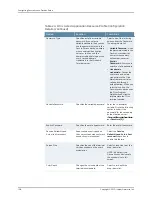
Table 25: Citrix Web Application Configuration Details
(continued)
Your Action
Options
Specify the Metaframe presentation servers to which you want to control access.
Click
Add
. When specifying servers, you can enter wildcards or IP ranges.
The device uses the values that you enter to automatically create a resource policy
that enables access to the necessary resources. They include:
•
If you select either
Java ICA Client with
or
without Web Interface
, the device creates
a Java ACL resource policy that enables Java applets to connect to the specified
Metaframe servers.
•
If you select
Non-Java ICA Client with Web Interface
, and then you select
ICA client
connects over WSAM or JSAM
, the device creates a corresponding SAM resource
policy that enables users to access the specified Metaframe servers.
•
If you select
Non-Java ICA Client with Web Interface
, and then you select
ICA client
connects over CTS
, the device creates corresponding Terminal Services and Java
resource policies that enable users to access the specified Metaframe servers.
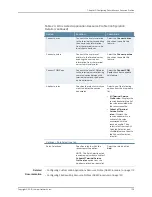
MetaFrame servers
Enable this check box to re-sign the specified resources using the certificate uploaded
after selecting
System > Configuration > Certificates > Code-signing Certificates
page.
NOTE: This option is for Java ICA clients only. Enable this option only if you have
deployed Citrix using a Java ICA client.
When you select this option, the device uses all of the “allow” values that you enter in
the resource profile’s Web access control autopolicy to automatically create a
corresponding code-signing resource policy. Within this policy, the device uses the
specified Web resources to create a list of trusted servers.
Sign applets with uploaded
code-signing certificate(s)
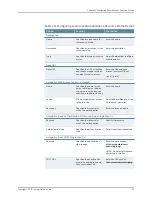
Enable this check box to allow users to access local resources such as printers and
drives through their Citrix Web interface sessions. Select one of the following options
after enabling this option:
•
Select
Connect printers
if you want to enable the user to print information from the
terminal server to the local printer.
•
Select
Connect drives
if you want to enable the user to copy information from the
terminal server to the local client directories.
•
Select
Connect COM Ports
if you want to enable communication between the
terminal server and devices on the user’s serial ports.
Configure access to local resources
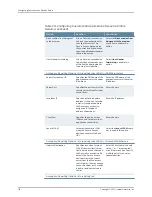
Enable this check box to create a policy that allows or denies users access to the
resource specified in the Web Interface (NFuse) URL box. By default, the device
automatically creates a policy for you that enables access to the resource and all of
its subdirectories.
Autopolicy: Web Access Control
Select the roles to which the Citrix resource profile applies.
Roles
111
Copyright © 2010, Juniper Networks, Inc.
Chapter 9: Configuring Secure Access Resource Profiles
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...