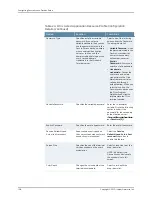
Table 27: Configuring File Rewriting Resource Profiles Details
(continued)
Your Action
Function
Option
Enter the resource using the format:
\\server[\share[\path]].
Specifies the resource policy to
which this policy applies.
New
Resources
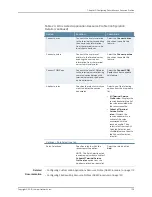
Select one of the following options:
•
Use Specified Credentials(Variable
Password)...
—Secure Access device uses
specified credentials with variable
password to pass to the Windows share
or directory.
•
Use Specified Credentials(Fixed
Password)...
—Secure Access device uses
specified credentials with fixed password
to pass to the Windows share or directory.
•
Prompt for user credentials
—Secure
Access device intermediates the share
challenge by presenting an authentication
challenge in the Secure Access device the
first time a user attempts to access the
share. The user enters the credentials and
the credentials are stored in the Secure
Access device. If the credentials later fail,
the Secure Access device again prompts
the user for the credentials.
Specifies the type of credentials
to pass to the Windows share or
directory.
Action
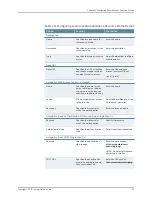
Enter a variable. For example,
<USERNAME> or a static username. For
example enter
administrator
to submit to
the Windows share or directory.
NOTE: When entering a variable, you may
also include a domain. For example,
yourcompany.net\<USERNAME>
Specifies a username to submit to
the Windows share or directory.
Username
Enter the variable password.
Specifies a variable password to
the Windows share or directory.
Variable
Password
Enter the static password.
Specifies a static password to the
Windows share or directory.
Password
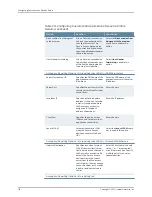
Bookmarks
Enter a name.
Specifies the name of the
bookmark.
Name
Enter the description.
Describes the bookmark.
Description
Enter the server name.
Specifies the server name.
Server
Enter the share name.
Specifies the share name.
Share
Copyright © 2010, Juniper Networks, Inc.
122
Configuring Secure Access Devices Guide
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...