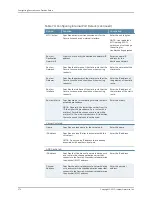
Table 84: IF–MAP Session-Export Policy Configuration Details
(continued)
Your Action
Function
Option
Select this action and the identity options appear.
•
Identity
—Enter the identity name. Identity is
normally specified as <Name>, which assigns
the user’s login name. Any combination of
literal text and context variables may be
specified.
•
Identity Type
—Select the identity type. If you
choose
Other
for Identity Type, enter a unique
identity type in the text box.
Specifies the applicable
identity.
Set IF-MAP
Identity
Roles tab
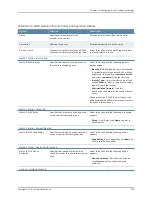
Select this action and the following role options
appear.
•
Copy matching roles
—Select this option to
copy all of the user roles that match the roles
specified in the Roles section of this policy into
the IF-MAP roles data.
•
Copy ALL roles
—Select this option to copy all
of the roles from the user session to the IF-MAP
capabilities data.
•
Set roles specified below
—Select this option
to set the specified roles. The Roles option
appears. From Roles, click
New
and enter a
specified role.
Specifies the applicable
roles.
Set IF-MAP
Roles
Capabilities tab
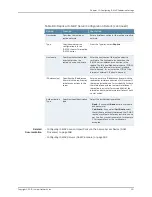
Select this action and the following role options
appear:
•
Copy matching roles
—Select this option to
copy all of the user roles that match the roles
specified in the Roles section of this policy into
the IF-MAP capabilities data.
•
Copy ALL roles
—Select this option to copy all
of the roles from the user session to the IF-MAP
roles data.
•
Set capabilities specified below
—Select this
option to set the specified capabilities. The
Capabilities option appears. From Capabilities,
click
New
and enter a specified capability.
Specifies the applicable
roles.
Set IF-MAP
Capabilities
Device Attributes tab
287
Copyright © 2010, Juniper Networks, Inc.
Chapter 20: Configuring IF-MAP Federation Settings
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...