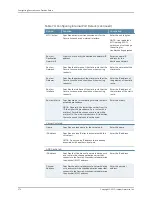
Table 76: Configuring Global Security Details
(continued)
Your Action
Function
Option
Select the
AES Medium (between
128-bit and 168-bit)
check box to
enable this feature.
Allows the Secure Access device to
use 168-bit or higher ciphers for
backend rewriter connections and the
device to provide preference to
256-bit AES encryption for backend
mail proxy SSL connections.
NOTE: This option is displayed only
when you select
Custom SSL Cipher
Selection
from the strength
drop–down list.
AES Medium
(between
128-bit and
168-bit)
Select the
RC4 Medium (between
128-bit and 168-bit)
check box to
enable this feature.
Allows Secure Access device to use
168-bit or higher ciphers for backend
rewriter connections and the device
provides preference to 256-bit AES
encryption for backend mail proxy SSL
connections.
NOTE: This option is displayed only
when you select
Custom SSL Cipher
Selection
from the strength
drop–down list.
RC4 Medium
(between
128-bit and
168-bit)
Select the
RC2 Medium (between
128-bit and 168-bit)
check box to
enable this feature.
Allows Secure Access device to use
168-bit or higher ciphers for backend
rewriter connections and device gives
preference to 256-bit AES encryption
for backend mail proxy SSL
connections.
NOTE: This option is displayed only
when you select
Custom SSL Cipher
Selection
from the strength
drop–down list.
RC2 Medium
(between
128-bit and
168-bit)
Select the
DES Low (less than
128-bit)
check box to enable this
feature.
Allows Secure Access device to use
168-bit or higher ciphers for backend
rewriter connections and the device
provides preference to 256-bit AES
encryption for backend mail proxy SSL
connections.
NOTE: This option is displayed only
when you select
Custom SSL Cipher
Selection
from the strength drop–
down list.
DES Low (less
than 128-bit)
Select the
Do not allow connections
from browsers that only accept
weaker ciphers
check box to enable
this feature.
Prevents a browser with a weak cipher
from establishing a connection.
Do not allow
connections
from browsers
that only
accept weaker
ciphers
Settings
263
Copyright © 2010, Juniper Networks, Inc.
Chapter 17: Configuring Secure Access System Management Features
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...