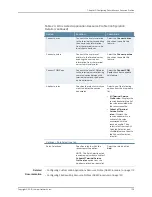
Table 27: Configuring File Rewriting Resource Profiles Details
(continued)
Your Action
Function
Option
Enter a suffix to the resource.
Adds a suffix to the resource if you
want to create links to
subdirectories of the resource
defined in the primary resource
profile.
Path
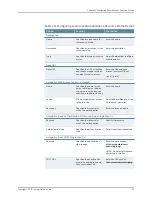
Select one of the following options:
•
Appear as bookmark on homepage and
file browsing
—Bookmark appears on
both a user’s welcome page and when
browsing network files.
•
Appear in file browsing only
—Bookmark
appears only when users are browsing
network files.
Displays the bookmark on a user’s
welcome page and when browsing
network files.
Appearance
Select one of the following options:
•
All File Profile roles
— Bookmark appears
both on a user’s welcome page and when
browsing network files.
•
Subset of File Profile roles
—Bookmark
appears only when users are browsing
network files.
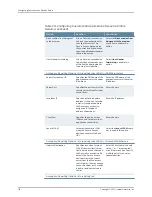
Specifies the roles to which you
want to display the bookmark.
Applies to
roles
`Bookmarks > Role Selections
Select the role, and then click
Add
.
Specifies the roles to which the
resource profile applies.
NOTE: The Role Selections tab is
enable only when you select the
Subset of File Profile roles
option
from the Applies to roles
drop-down list.
Roles
Selections
Related
Documentation
Configuring Windows Terminal Services (NSM Procedure) on page 124
•
•
Configuring a Telnet/SSH Resource Profile (NSM Procedure) on page 129
•
Configuring Custom Web Applications Resource Profile (NSM Procedure) on page 112
123
Copyright © 2010, Juniper Networks, Inc.
Chapter 9: Configuring Secure Access Resource Profiles
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...