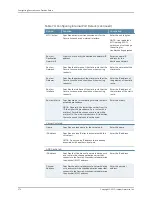
Table 76: Configuring Global Security Details
(continued)
Your Action
Function
Option
Enter the time.
Specifies the number of minutes you
want the Secure Access device to lock
out the IP address.
Lockout period
(minutes)
Enter the number of attempts.
Specifies the maximum number of
failed sign-in attempts to allow before
triggering the initial lockout.
Attempts
Enter the number of sign-in attempts
to allow per minute.
Specifies the number of failed sign-in
attempts to allow per minute.
Rate
Select the
Show last login time on
user's bookmark page
check box to
enable this feature.
Displays the day and time the user last
logged in to the system in the
bookmark page.
Show last login
time on user's
bookmark page
Select the
Show last login IP address
on user's bookmark page
check box
to enable this feature.
Displays the IP address when user last
logged in to the system in the
bookmark page.
Show last login
IP address on
user's
bookmark page
Select one of the following options
from the drop-down list:
•
Delete all cookies at session
termination (maximize
security)
—Secure Access device
deletes all cookies at session
termination.
•
Preserve cookies at session
termination
—Secure Access device
preserves cookies at session
termination.
Allows Secure Access device to set
persistent cookies on the user’s
machine to support functions such as
multiple sign-in, last associated realm,
and last sign-in URL. If you desire
additional security or privacy, you may
choose to not set them.
Delete all
cookies at
session
termination
Select any one of the following
options from the drop-down list:
•
Include session cookie in URL
(maximize compatibility)
—Secure
Access device includes session
cookie in URL.
•
Do not include session cookie in
URL (maximize security)
—Secure
Access device does not include the
session cookie in URL.
Allows Secure Access device to
include the user session cookie in the
URL that launches JSAM or a Java
applet. By default, this option is
enabled, but if you have concerns
about exposing the cookie in the URL,
you can disable this feature.
Include IVE's
session cookie
in URL
Select
SAML 1.0
or
SAML 1.1
from the
drop-down list.
Allows you to specify the SAML
protocol and schema.
SAML version
Related
Documentation
Configuring Sensors (NSM Procedure) on page 265
•
•
Configuring the Network Communications Protocol (NSM Procedure) on page 257
Copyright © 2010, Juniper Networks, Inc.
264
Configuring Secure Access Devices Guide
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...