Creating a Custom Expression for Sensor Settings (NSM Procedure)
Custom expressions are strings that are made up of variables, operators, and
subexpressions all concatenated together. These operators and variables are provided
through an expressions dictionary.
To create a custom expression for sensor settings:
1.
In the NSM navigation tree, select
Device Manager
>
Devices
.
2.
Click the
Device Tree
tab, and then double-click the Secure Access device for which
you want to configure sensor settings.
3.
Click the
Configuration
tab. In the configuration tree, select
System > Configuration
> Sensors
.
4.
Select the
Sensor Events
tab.
5.
Click
New
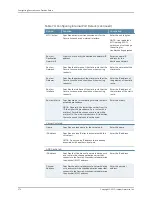
to create a custom expression. The Custom Expression editor appears. On
the left side of the editor is the Expression Dictionary, which includes the following
custom expression building blocks:
•
Logical Operators: This node consists of logical operators that are used to build
expressions. Select a logical operator and click the
Insert Expression
button to
insert logical operators in expressions.
•
Prebuilt Expressions: This node consists of expressions that function as templates
for custom expressions. Select a prebuilt expression and click the
Insert Expression
button. The prebuilt expression is displayed in the Expression area. Modify the values
to create your own custom expression.
•
Variables: This node consists of variables. When a variable is selected, the conditional
operators that can be applied to this variable are listed in the center of the Custom
Expressions editor. Also, some variables have extensions that are displayed in the
drop-down list next to the variable. Double-click a variable to display its description
and example usage. Click the example variable to insert it in the Expression area.
•
IF-MAP Variables: This node consists of IF-MAP variables. Double-click a IF-MAP
variable to display its description and example usage. Click the IF-MAP variable
example to insert it in the Expression area.
•
Juniper IDP Variables: This node consists of Juniper IDP variables. Double-click a
Juniper IDP variable to display its description and example usage. Click the Juniper
IDP variable example displayed to insert it in the Expression area.
NOTE:
Refer to the Juniper Networks Secure Access Administration Guide
for more information on variables and writing custom expressions.
6.
Enter a name for the custom expression.
Copyright © 2010, Juniper Networks, Inc.
268
Configuring Secure Access Devices Guide
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...