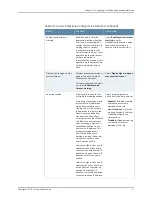
Table 9: IP Alias Configuration Details
Your Action
Function
Option
Select the VLAN you want to use from the VLAN
list, if you have defined VLAN ports on your
system.
NOTE: If an end user is mapped to multiple roles
and the Secure Access device merges roles, the
Secure Access device associates the source IP
address configured for the first role in the list with
the merged role.
Specifies role-based source IP
aliases. If you want to direct
traffic to specific sites based on
roles, you can define a source IP
alias for each role.
VLAN
Select a source IP address from the list.
NOTE: You can specify the same source IP
address for multiple roles. You cannot specify
multiple source IP addresses for one role.
Configures virtual ports you
define for the internal interface
source IP address.
Select
Source IP
Related
Documentation
Configuring Secure Access General Session Options (NSM Procedure) on page 39
•
•
Creating and Configuring Secure Access Device Administrator Roles (NSM Procedure)
on page 43
•
Creating and Applying a Secure Access Device Template on page 29
•
Verifying Imported Device Configurations on page 19
Configuring Secure Access General Session Options (NSM Procedure)
To specify session time limits, roaming capabilities, session and password persistency,
request follow-through options, and idle timeout application activity, follow these steps:
1.
In the NSM navigation tree, select
Device Manager
>
Devices
. Click the
Device Tree
tab, and then double-click the Secure Access device for which you want to configure
user roles.
2.
Click the
Configuration
tab, and select
Users
>
User Roles
. The corresponding
workspace appears.
3.
Click the
New
button and the New dialog box appears.
4.
Click
General
>
Session Options
to add or modify settings as specified in Table 10 on
page 40.
5.
Click one:
•
OK
—Saves the changes.
•
Cancel
—Cancels the modification.
39
Copyright © 2010, Juniper Networks, Inc.
Chapter 6: Configuring User Roles and Administrator Roles
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...