Configuring Secure Meetings (NSM Procedure)
Unlike other access features, Secure Meeting does not have a resource policy. Instead,
you configure system-level settings that apply to all roles for which this feature is enabled.
You can:
•
Specify session lifetime limits for meetings.
•
Enable daylight savings adjustments to scheduled meetings.
•
Specify the maximum color depth of meeting presentations.
•
Enable automatic email notifications for users who are invited to meetings scheduled
through the Secure Access device end user console.
•
Define the MySecureMeeting URL.
To configure secure meetings:
1.
In the NSM navigation tree, select
Device Manager > Devices
. Click the
Device Tree
tab, and then double-click the Secure Access device for which you want to configure
secure meetings.
2.
Click the
Configuration
tab, and select
System > Configuration > Secure Meeting
.
The corresponding workspace appears.
3.
Add or modify settings as specified in Table 75 on page 259.
4.
Click one:
•
OK
—Saves the changes.
•
Cancel
—Cancels the modification.
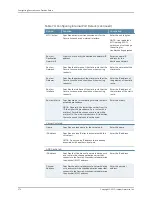
Table 75: Configuring Secure Meeting Details
Your Action
Function
Option
Enter the time.
Specifies the number of minutes a meeting session may
remain idle before ending.
Idle Timeout
(minutes)
Enter the time.
Specifies the number of minutes a meeting session may
remain open before ending.
Max. Session Length
(minutes)
Select
Enable Upload Logs
to enable this
feature.
NOTE: If you select the Upload Logs
option, you must also use settings in the
System > Log/Monitoring > Client Logs >
Settings
page of the admin console to
enable client-side logging.
Allows non-Secure Access device users to upload meeting
logs.
Enable Upload Logs
259
Copyright © 2010, Juniper Networks, Inc.
Chapter 17: Configuring Secure Access System Management Features
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...