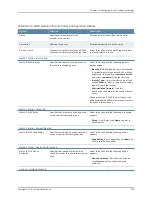
Table 86: Replica IF–MAP Server Configuration Details
(continued)
Your Action
Function
Option
Enter a brief description for the replica or replica
network.
Describes the replica or
replica network.
Description
From the Type list, select
Replica
.
Specifies whether the
configuration is for an
IF-MAP client or for a replica
IF-MAP server.
Type
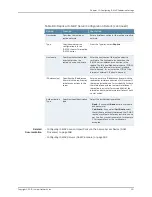
Enter the hostname of the replica’s device
certificate. The hostname is used when this
IF-MAP server initiates a connection to the
replica. The fully qualified domain name (FQDN)
of the replica's internal or external interface
should be used; for a cluster, the FQDN of the
internal or external VIP should be used.
Specifies the hostname that
exactly matches the
replica’s device certificate.
Hostname
Enter one or more IP addresses from which the
replica may initiate connections to this server. If
the replica is standalone, for survivability list both
the internal and external network interfaces. If
the replica is a cluster, for survivability list the
internal and external network interfaces of both
cluster nodes.
Specifies the IP addresses
from which the replica may
initiate connections to this
server.
IP Address(es)
Select the authentication method:
•
Basic
—If you select
Basic
, enter a username
and password.
•
Certificate
—If you select
Certificate
, select
the certificate authority that issued the IF-MAP
replica’s certificate. Enter any restrictions, one
per line. If any restrictions match, for example
CN=ic.example.com, the certificate is
accepted.
Specifies the authentication
type.
Authentication
Type
Related
Documentation
•
Configuring IF-MAP Session Import Policy on the Secure Access Device (NSM
Procedure) on page 288
•
Configuring IF-MAP Servers (NSM Procedure) on page 283
291
Copyright © 2010, Juniper Networks, Inc.
Chapter 20: Configuring IF-MAP Federation Settings
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...