xStack® DGS-3120 Series Layer 3 Managed Gigabit Ethernet Switch Web UI Reference Guide
9
DDM (RI and EI Mode Only)
This folder contains windows that perform Digital Diagnostic Monitoring (DDM) functions on the Switch. There are
windows that allow the user to view the digital diagnostic monitoring status of SFP modules inserting to the Switch
and to configure alarm settings, warning settings, temperature threshold settings, voltage threshold settings, bias
current threshold settings, TX power threshold settings, and Rx power threshold settings.
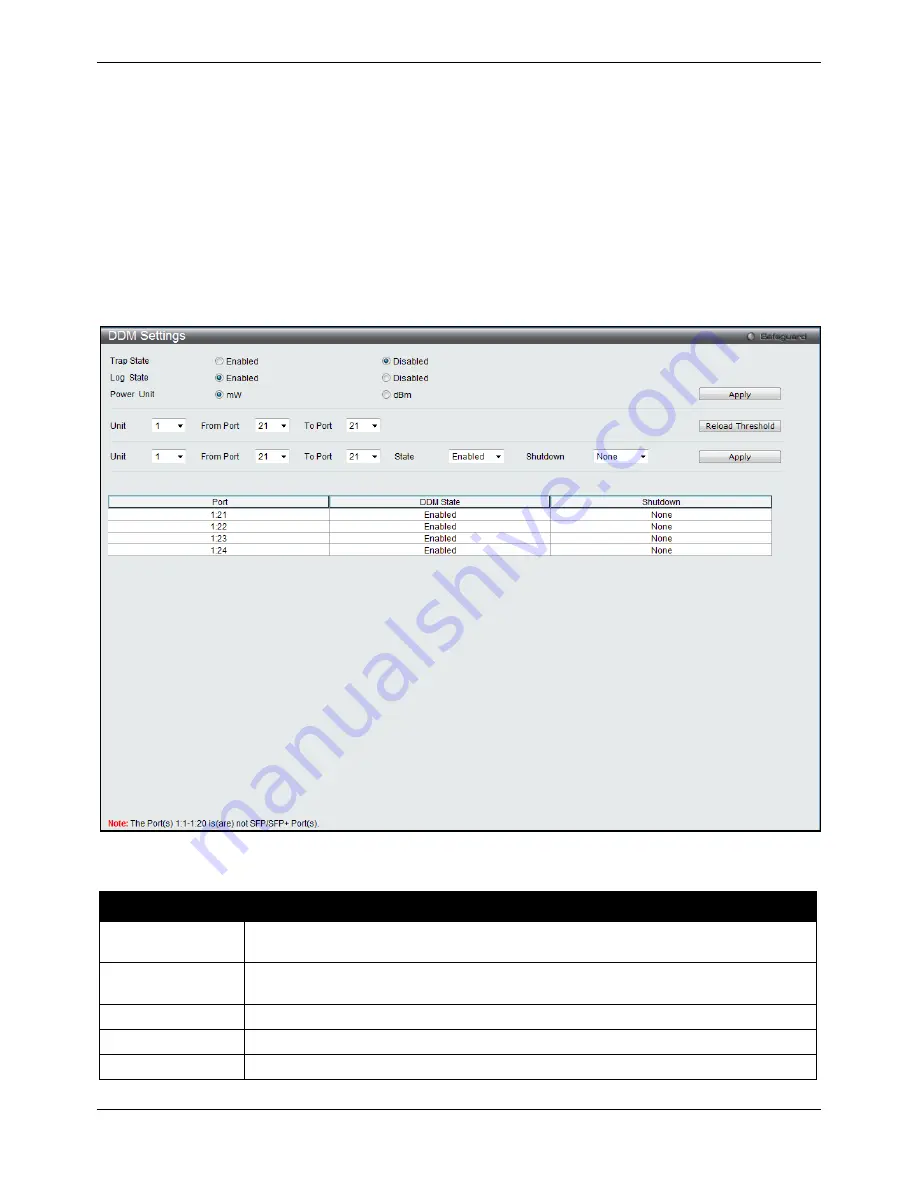
DDM Settings
The window is used to configure the action that will occur for specific ports when an exceeding alarm threshold or
warning threshold event is encountered.
To view the following window, click
System
Configuration > Port Configuration > DDM > DDM Settings
, as
shown below:
Figure 2-5 DDM Settings window
The fields that can be configured are described below:
Parameter
Description
Trap State
Specify whether to send the trap, when the operating parameter exceeds the alarm or
warning threshold.
Log State
Specify whether to send the log, when the operating parameter exceeds the alarm or
warning threshold.
Unit
Select the unit to be configured.
(EI Mode Only)
From Port / To Port
Select a range of ports to be configured.
State
Use the drop-down menu to enable or disable the DDM state
Summary of Contents for xStack DGS-3120 Series
Page 1: ......