xStack® DGS-3120 Series Layer 3 Managed Gigabit Ethernet Switch Web UI Reference Guide
102
Discarding
Discarding
Listening
No
No
Learning
Learning
Learning
No
Yes
Forwarding
Forwarding
Forwarding
Yes
Yes
RSTP is capable of a more rapid transition to a forwarding state - it no longer relies on timer configurations - RSTP
compliant bridges are sensitive to feedback from other RSTP compliant bridge links. Ports do not need to wait for
the topology to stabilize before transitioning to a forwarding state. In order to allow this rapid transition, the protocol
introduces two new variables: the edge port and the point-to-point (P2P) port.
Edge Port
The edge port is a configurable designation used for a port that is directly connected to a segment where a loop
cannot be created. An example would be a port connected directly to a single workstation. Ports that are
designated as edge ports transition to a forwarding state immediately without going through the listening and
learning states. An edge port loses its status if it receives a BPDU packet, immediately becoming a normal
spanning tree port.
P2P Port
A P2P port is also capable of rapid transition. P2P ports may be used to connect to other bridges. Under
RSTP/MSTP, all ports operating in full-duplex mode are considered to be P2P ports, unless manually overridden
through configuration.
802.1D-1998/802.1D-2004/802.1Q-2005 Compatibility
MSTP or RSTP can interoperate with legacy equipment and is capable of automatically adjusting BPDU packets to
802.1D-1998 format when necessary. However, any segment using 802.1D-1998 STP will not benefit from the
rapid transition and rapid topology change detection of MSTP or RSTP. The protocol also provides for a variable
used for migration in the event that legacy equipment on a segment is updated to use RSTP or MSTP.
The Spanning Tree Protocol (STP) operates on two levels:
1. On the switch level, the settings are globally implemented.
2. On the port level, the settings are implemented on a per-user-defined group of ports basis.
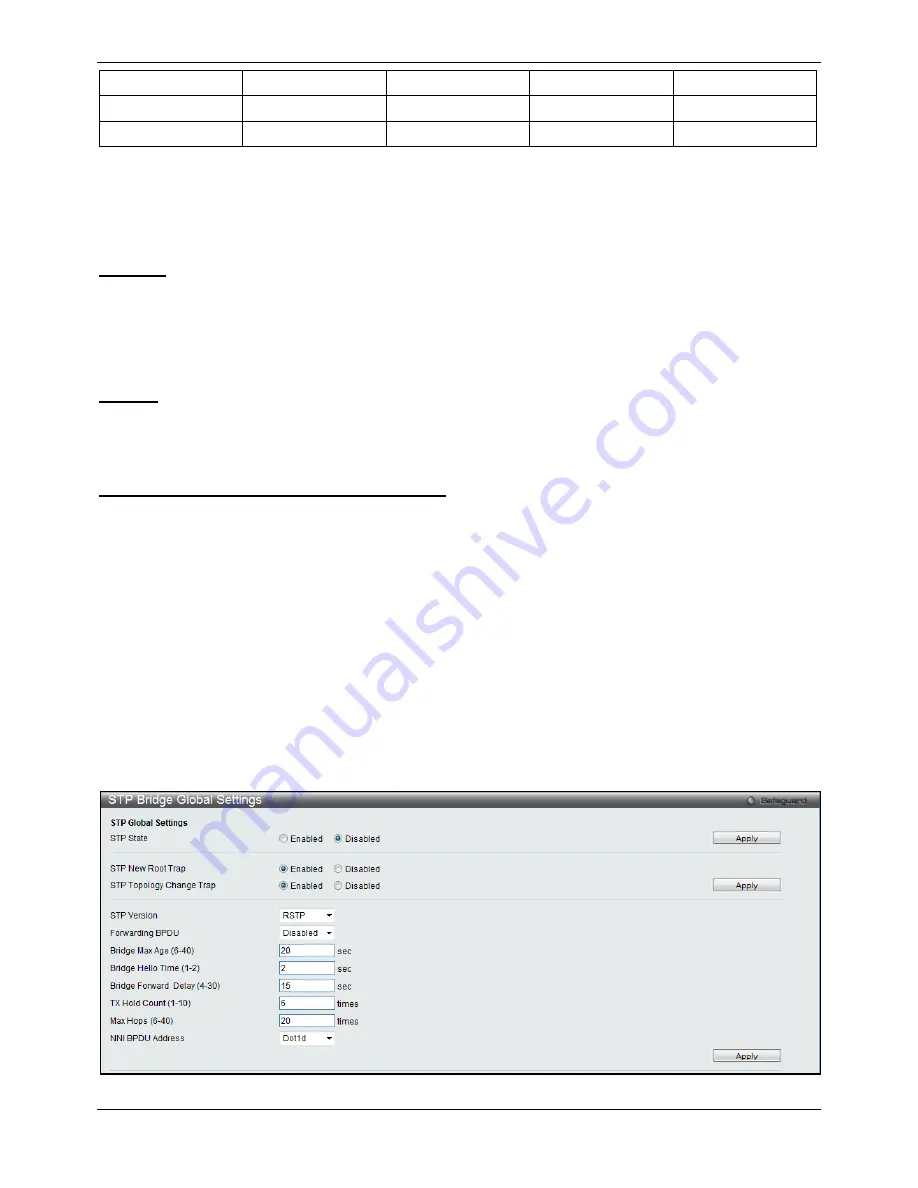
STP Bridge Global Settings
This window is used to configure the STP bridge global parameters.
To view the following window, click
L2 Features > Spanning Tree > STP Bridge Global Settings
, as shown
below:
Figure 4-35 STP Bridge Global Settings window
Summary of Contents for xStack DGS-3120 Series
Page 1: ......






























