524
Fabric OS Administrator’s Guide
53-1001763-02
FIPS mode configuration
D
LDAP in FIPS mode
You can configure your Microsoft Active Directory server to use LDAP while in FIPS mode. There is
no option provided on the switch to configure TLS ciphers for LDAP in FIPS mode. However, the
LDAP client checks if FIPS mode is set on the switch and uses the FIPS-compliant TLS ciphers for
LDAP. If the FIPS mode is not set and the Microsoft Active Directory server is configured for FIPS
ciphers, it uses FIPS-compliant ciphers.
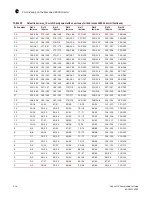
Table 104
lists the differences between FIPS and non-FIPS modes of operation.
Setting up LDAP for FIPS mode
1. Set the switch authentication mode and add your LDAP server by using the commands in the
example below. Provide the Fully Qualified Domain Name (FQDN) of the Active Directory server
for the hostname parameter while configuring LDAP.
Example of setting up LDAP for FIPS mode
switch:admin> aaaconfig --add GEOFF5.ADLDAP.LOCAL -conf ldap -d adldap.local
-p 389 -t 3
switch:admin> aaaconfig --authspec "ldap;local"
switch:admin> aaaconfig –show
RADIUS CONFIGURATIONS
=====================
RADIUS configuration does not exist.
LDAP CONFIGURATIONS
===================
Position : 1
Server : GEOFF5.ADLDAP.LOCAL
Port : 389
Domain : adldap.local
Timeout(s) : 3
Primary AAA Service: LDAP
Secondary AAA Service: Switch database
TABLE 104
FIPS and non-FIPS modes of operation
FIPS mode
non-FIPS mode
•
The CA who issued the Microsoft Active Directory
server certificate must be installed on the switch.
•
There is no mandatory CA certificate
installation on the switch.
•
Configure FIPS compliant TLS ciphers [TDES-168,
SHA1 and RSA-1024] on Microsoft Active Directory
server. The host needs a reboot for the changes to
take effect.
•
On the Microsoft Active Directory server, there
is no configuration of the FIPS compliant TLS
ciphers.
•
The switch uses FIPS-compliant ciphers regardless of
Microsoft Active Directory server configuration. If the
Microsoft Active Directory server is not configured for
FIPS ciphers, authentication will still succeed.
•
The Microsoft Active Directory server certificate
is validated if the CA certificate is found on the
switch
•
The Microsoft Active Directory server certificate is
validated by the LDAP client. If the CA certificate is not
present on the switch then user authentication will
fail.
•
If Microsoft Active Directory server is
configured for FIPS ciphers and the switch is in
non-FIPS mode then user authentication will
succeed.
Summary of Contents for 53-1001763-02
Page 1: ...53 1001763 02 13 September 2010 Fabric OS Administrator s Guide Supporting Fabric OS v6 4 0 ...
Page 4: ...iv Fabric OS Administrator s Guide 53 1001763 02 ...
Page 24: ...xxiv Fabric OS Administrator s Guide 53 1001763 02 ...
Page 28: ...xxviii Fabric OS Administrator s Guide 53 1001763 02 ...
Page 32: ...xxxii Fabric OS Administrator s Guide 53 1001763 02 ...
Page 40: ...xl Fabric OS Administrator s Guide 53 1001763 02 ...
Page 42: ...2 Fabric OS Administrator s Guide 53 1001763 02 ...
Page 54: ...14 Fabric OS Administrator s Guide 53 1001763 02 High availability of daemon processes 1 ...
Page 74: ...34 Fabric OS Administrator s Guide 53 1001763 02 Basic connections 2 ...
Page 102: ...62 Fabric OS Administrator s Guide 53 1001763 02 Audit log configuration 3 ...
Page 214: ...174 Fabric OS Administrator s Guide 53 1001763 02 Management interface security 7 ...
Page 228: ...188 Fabric OS Administrator s Guide 53 1001763 02 Brocade configuration form 8 ...
Page 276: ...236 Fabric OS Administrator s Guide 53 1001763 02 Creating a logical fabric using XISLs 10 ...
Page 404: ...364 Fabric OS Administrator s Guide 53 1001763 02 ...
Page 440: ...400 Fabric OS Administrator s Guide 53 1001763 02 Performance data collection 17 ...
Page 480: ...440 Fabric OS Administrator s Guide 53 1001763 02 F_Port masterless trunking 19 ...
Page 494: ...454 Fabric OS Administrator s Guide 53 1001763 02 Buffer credit recovery 20 ...
Page 574: ...534 Fabric OS Administrator s Guide 53 1001763 02 Hexadecimal overview E ...