Action and Event Tables
92
8.4.2 Multiple Actions on a Single Alarm
In some instances you may want more than one action to occur when a single alarm is detected.
For instance, a hacking attempt may be reported to two different people. In that case, the
DOLIST command is used. The first line gives the general form of the alarm to be used as the
trigger. The following lines have the same mnemonic but with an extension which denotes an
order of action. In the example given below, .1 and .2 are added to show two subsequent actions
to be taken. When the .AUTHFAIL alarm is detected, the ASG Guard/ASG Guard Plus "phones
home" and pages, sending the alarm and the comments.
NOTE:
DOLIST cannot be nested (a DOLIST inside another DOLIST).
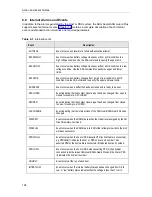
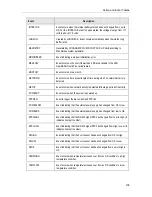
ALARM
ACTION
PARAMETER
COMMENTS
.AUTHFAIL
DOLIST
HACKER ALERT
.AUTHFAIL.1
PHONHOME
.AUTHFAIL.2
PAGE
NOTE:
The actions in a DOLIST are dispatched in the order shown in the Action Table, but they
are not necessarily executed in that order. For example, the PHONHOME action may be
rescheduled if the modem is already in use. In that case, the system will begin to execute
the PAGE action without waiting for PHONHOME to complete.
8.5 Planning the Action Table
Before you start to build your Action Table, you should determine which alarm conditions to
monitor and decide what action should be taken for each alarm condition.
A worksheet is provided to assist you in planning which alarm/status messages should be
monitored by the ASG Guard/ASG Guard Plus, and what actions should be taken by the ASG
Guard/ASG Guard Plus when they are received. To help guide you, we have also provided an
example of a filled in worksheet at the end of this section.
NOTE:
You must have at least Sysop 2 level access to add, delete or change Action Table items.
1.
Determine which alarm conditions to monitor.
Examine the types of alarms to which you or your staff respond on a regular basis and then
define them in the worksheet.
In the example worksheet, note that the "SYS000" (System Reload) and "INI000" (System
Reload Result) are among the types of messages that are being monitored. Other messages
are BSD090 (Power Failure), the Digital Trunking Alarms (DTA and DTI), and the ERR series
of alarms.
2.
Decide what action is to be taken when a particular alarm condition is received.
Based on the action, you should then "match" this action to the alarm you select.
In the worksheet example, the alarm "SYS000" has been "matched" with the Action Routine
"SCHEDULE" (which schedules a future action). The SCHEDULE routine requires that you
define the action to be taken as well as the time at which that will occur. In the example, the
Содержание Lucent Technologies Access Security Gateway Guard
Страница 12: ...x Page intentionally left blank ...
Страница 28: ...ASG Guard Overview 16 Page intentionally left blank ...
Страница 36: ...Physical Connections 24 Page intentionally left blank ...
Страница 60: ...Modem Port Setup 48 Page intentionally left blank ...
Страница 82: ...Modifying the User Database 70 Page intentionally left blank ...
Страница 106: ...Action and Event Tables 94 ACTION TABLE WORKSHEET Alarm Message or Internal Event Action Routine Routine Parameters ...
Страница 120: ...Action and Event Tables 108 Page intentionally left blank ...
Страница 158: ...User Connectivity 146 Page intentionally left blank ...
Страница 188: ...Log Functions 176 Page intentionally left blank ...
Страница 236: ...Troubleshooting 224 Page intentionally left blank ...
Страница 252: ...Internal Battery Replacement 240 Page intentionally left blank ...
Страница 258: ...Glossary of Command References 246 Page intentionally left blank ...