| Aspera Sync |
237
-C
,
--continuous
Run continuous synchronization. Default: disabled.
Usage notes:
• Continuous mode is supported only when the file source is Windows or Linux. Continuous pulls
can be run from any operating system if the source is Windows or Linux. Continuous push can
be run only by Windows or Linux. Continuous bidi requires that both the Aspera Sync client and
server are Windows or Linux.
• If a file is open,
async
cannot transfer the file due to sharing violations and might ignore the
file if it is closed without changes. To specify the maximum number of retries after a sharing
violation, use with
--sharing-retry-max
. To enable periodic scans that detect when an
opened file has been closed and is ready for transfer, use with
--scan-interval
.
• If you receive an
inotify
error when attempting to run continuous synchronization, see
Troubleshooting Continuous Aspera Sync Errors
on page 266.
-c
cipher
,
--cipher=
cipher
Encrypt file data with encryption algorithm. Aspera supports three sizes of AES cipher keys (128,
192, and 256 bits) and supports two encryption modes, cipher feedback mode (CFB) and Galois/
counter mode (GCM). The GCM mode encrypts data faster and increases transfer speeds compared
to the CFB mode, but the server must support and permit it.
Cipher rules
The encryption cipher that you are allowed to use depends on the server configuration and the
version of the client and server:
• When you request a cipher key that is shorter than the cipher key that is configured on the server,
the transfer is automatically upgraded to the server configuration. For example, when the server
setting is AES-192 and you request AES-128, the server enforces AES-192.
• When the server requires GCM, you must use GCM (requires version 3.9.0 or newer) or the
transfer fails.
• When you request GCM and the server is older than 3.8.1 or explicity requires CFB, the transfer
fails.
• When the server setting is "any", you can use any encryption cipher. The only exception is when
the server is 3.8.1 or older and does not support GCM mode; in this case, you cannot request
GCM mode encryption.
• When the server setting is "none", you must use "none". Transfer requests that specify an
encryption cipher are refused by the server.
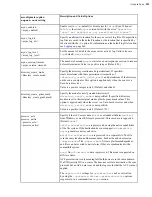
Cipher Values
Value
Description
Support
aes128
aes192
aes256
Use the GCM or CFB encryption
mode, depending on the server
configuration and version (see cipher
negotiation matrix).
All client and server versions.
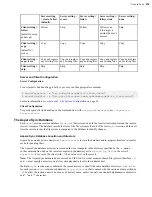
aes128cfb
aes192cfb
aes256cfb
Use the CFB encryption mode.
Clients version 3.9.0 and newer, all
server versions.
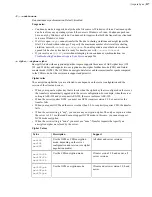
aes128gcm
aes192gcm
aes256gcm
Use the GCM encryption mode.
Clients and servers version 3.9.0 and
newer.