29
TANDBERG
FieldView Administrator Guide
D14098.02 June 2008
Anonymous login permitted.
Check to display a
Skip
button on the User
Authentication window so that the login can be bypassed. The user is named
‘anonymous’ in this case.
Force login when resuming from Standby.
Check to open the User
Authentication window whenever the TANDBERG FieldView Device wakes from
Standby.
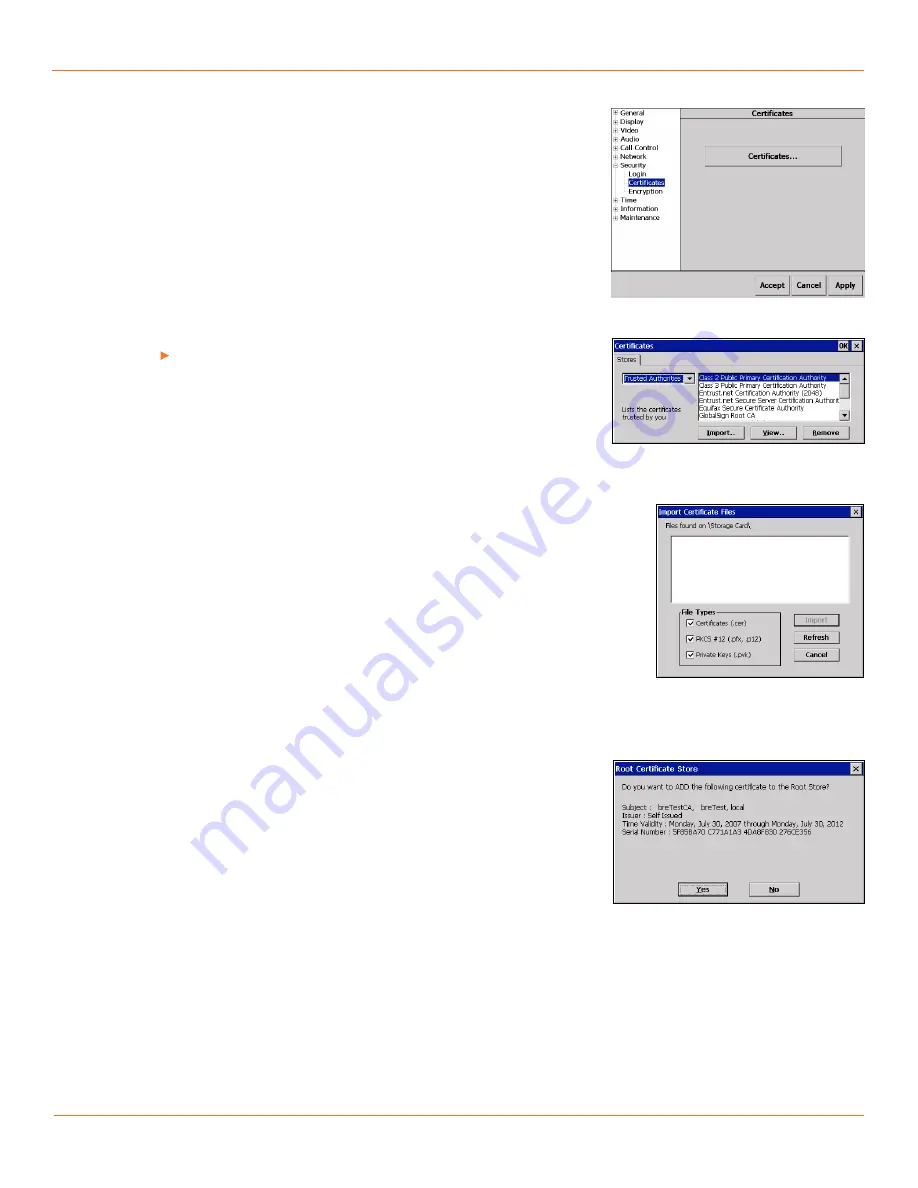
Security>Certificates
Certificates button.
Tap
Certificates
(see Fig. 4-34) to open the Certificates
window to view and import security certificates.
Note that when using certificates the TANDBERG FieldView Device date and
time must be current to allow successful verification of the certificate.
See the section
Wireless Network Properties
for more information.
Import… button.
Tap the
Import…
button in the Certificates window to
import certificate files (to the selected Store) from an SD card for use with
network authentication (see Fig. 4-35).
The TANDBERG FieldView Device searches the storage card root (\Storage
Card\) and a top-level Certificates directory for compatible files (\Storage
Card\Certificates\). You must confirm the import. See Fig. 4-36 and Fig. 4-37.
Note:
When viewing the SD card on a PC the \Storage Card prefix will be
replaced by the drive letter associated with the SD card. e.g. F:\Certificates.
File types allowed for import are:
•
Certificates (
.cer
)
are individual X.509 certificate objects. They contain
a public key, but not a private key. A password is not required to import or
export these files.
•
PKCS #12 (.
pfx, .p12
)
(Personal Information Exchange #12) files may
contain multiple certificates and private keys. The file is protected by a
password set when the file is created. The password is required for import.
•
Private Keys (.
pvk
)
are single passphrase protected Windows private key
files. When creating or exporting these files, users will be prompted for a
passphrase. The exact passphrase is needed to import the file.
Stores list
Certificates can be imported to the following three logical stores:
•
My Certificates
contains individual certificates for users, machine, or
service. For example,
My Certificates
could contain a user certificate
issued by a certificate authority (CA) for authentication on an EAP-TLS
configured network.
•
Trusted Authorities
contains the certificate from trusted root authorities.
All certificates in this store should have the same subject and issuer (self-
signed).
•
Other Authorities
stores all other certificate types. This can include
intermediate CA certificates.
Note:
Since PKCS #12 files may contain several certificate and private key
files, the decision on where to import them is made automatically by the
software. For this reason, it doesn’t matter which certificate store is currently
selected.
Fig. 4-34 Security>Certificates Page
Fig. 4-35 Certificates window
Fig. 4-36 Import Certificate Files
Fig. 4-37 Root Certificate Store confirmation
Chapter 4






























