Use Cases/Tutorials
p. 172
How to protect your G-RACK 12 from (unwanted) network traffic.
Use the Firewall configuration to screen unwanted traffic. The G-RACK 12 has a built-in network
firewall in the OS that filters traffic between the server and incoming network traffic.
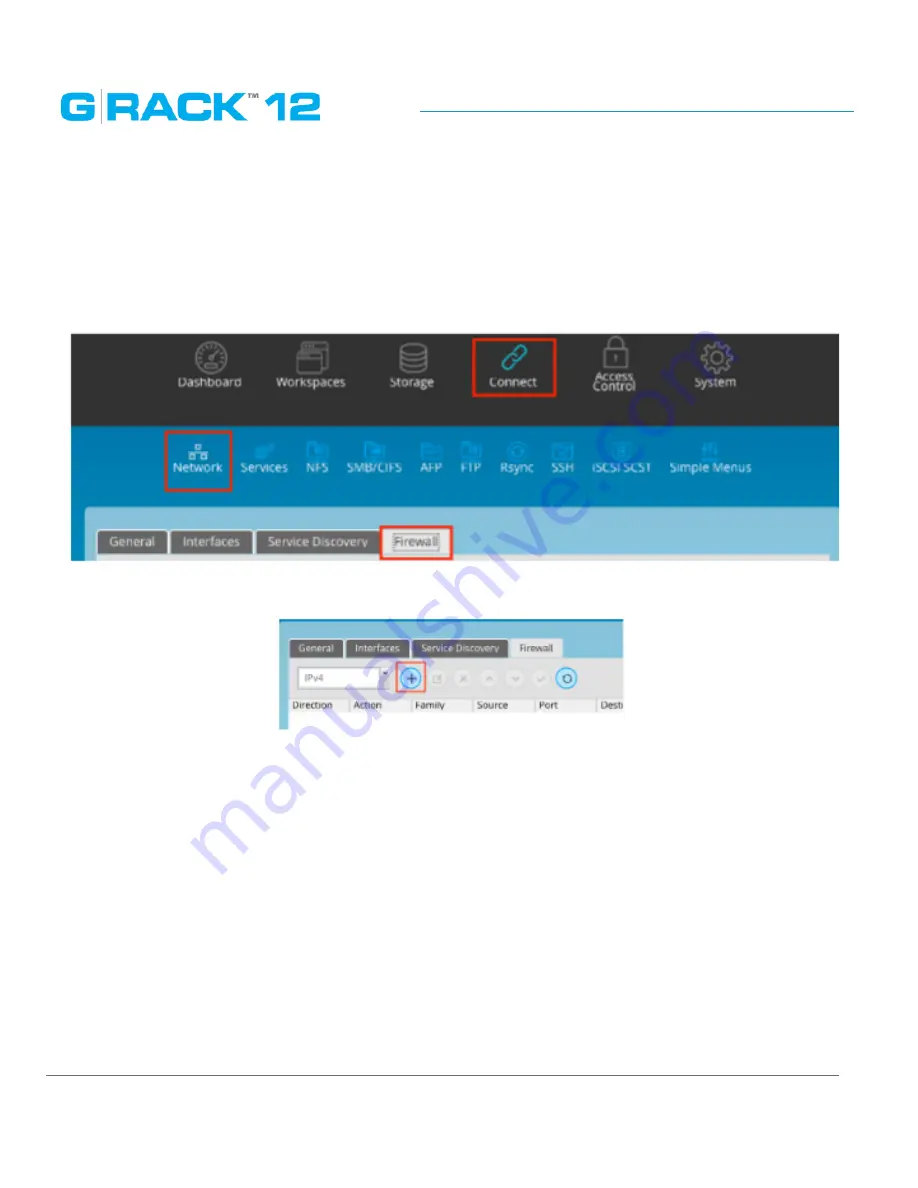
1. Press the Network option.
2. You will be presented with 4 tabs. (General, Interfaces, Service Discovery, and Firewall)
3. Select select the Firewall tab.
4. Chose if you are creating an IPv4 or IPv6 rule.
5. Press the Plus (+) to open the rules dialog.
6. Select direction of the rule:
•
INPUT for inbound connections
•
OUTPUT for outbound connections
7. Choose action for a packet which matches the rule:
•
ACCEPT -- allow the packet to pass over
•
REJECT -- drop the packet and send ICMP reject message back to the sender which prevents
hanging of the connection
•
DROP -- drop the packet
•
LOG -- just log the packet in the journal
•
Nothing -- do nothing (useful for debugging)
8. Specify source and destination port and address. Destination address can be either a network
IP address (with /mask), a IP range or a plain IP address. A ‚!’ argument before the address
specification inverts the sense of the address. Ports can be specified either by number (e.g. 80 for
Summary of Contents for G-RACK 12
Page 1: ......
Page 2: ...Copyrights...
Page 4: ...Introduction...
Page 9: ...Getting Started...
Page 12: ...Getting Started p 12 Front View Rear View...
Page 32: ...Administrative Tool...
Page 48: ...Administrative Tool p 48 Extended information from smartctl utility...
Page 92: ...Administrative Tool p 92 Comment Optional comment text box...
Page 109: ...Administrative Tool p 109 Example error message...
Page 124: ...Administrative Tool p 124 Memory usage Network interfaces...
Page 130: ...Hardware Description...
Page 159: ...Use Cases Tutorials...
Page 180: ...Use Cases Tutorials p 180...
Page 184: ...Use Cases Tutorials p 184 You need to click the enable slider to activate this option...
Page 191: ...Use Cases Tutorials p 191 Lastly a review is presented before the shares are created...
Page 192: ...Use Cases Tutorials p 192 Once you confirm the process starts...
Page 215: ...Use Cases Tutorials p 215 6 The RAID is ready...
Page 221: ...iSCSI Essentials...
Page 228: ...iSCSI Essentials p 228 Links and references https en wikipedia org wiki ISCSI...
Page 234: ...Troubleshooting...
Page 247: ...F A Q...
Page 272: ...Technical Support Warranty...
Page 283: ...Glossary...
Page 289: ...Appendices...






























