AWS Storage Gateway User Guide
Using Identity-Based Policies (IAM Policies)
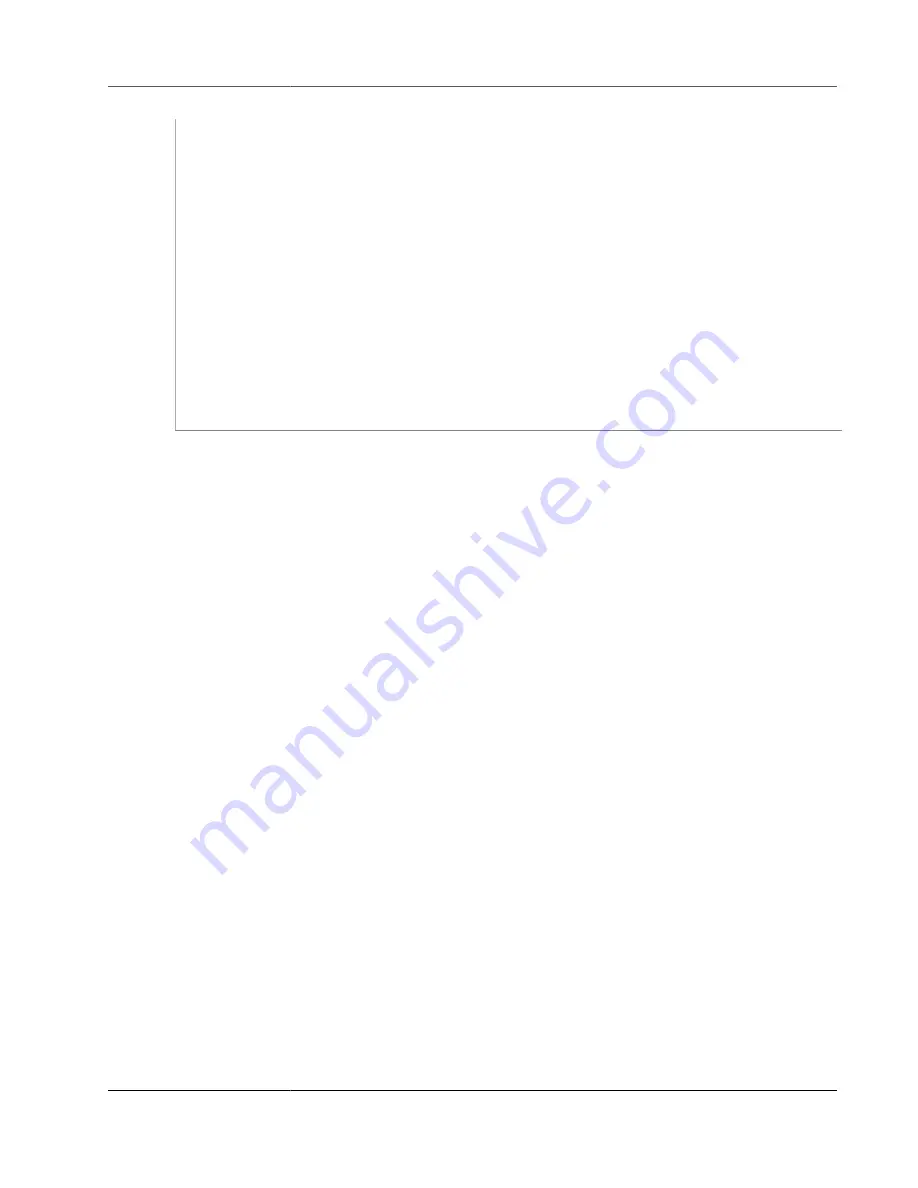
"Statement": [
{
"Sid": "AllowsSpecifiedActionsOnAllGateways",
"Effect": "Allow",
"Action": [
"storagegateway:ActivateGateway",
"storagegateway:ListGateways"
],
"Resource": "arn:aws:storagegateway:us-west-2:
account-id
:gateway/*"
},
{
"Sid": "AllowsSpecifiedEC2ActionsOnAllGateways",
"Effect": "Allow",
"Action": [
"ec2:DescribeSnapshots",
"ec2:DeleteSnapshot"
],
"Resource": "*"
}
]
}
The policy has two statements (note the
Action
and
Resource
elements in both the statements):
• The first statement grants permissions for two Storage Gateway actions
(
storagegateway:ActivateGateway
and
storagegateway:ListGateways
) on a gateway
resource using the
Amazon Resource Name (ARN)
for the gateway. The ARN specifies a wildcard
character (*) because you don't know the gateway ID until after you create a gateway.
Note
ARNs uniquely identify AWS resources. For more information, see
(ARNs) and AWS Service Namespaces
AWS General Reference
.
The wildcard character (*) at the end of the gateway ARN means that this statement can match
any gateway ID. In this case, the statement allows the
storagegateway:ActivateGateway
and
storagegateway:ListGateways
actions on any gateway in the specified region,
us-west-2
,
and the specified ID identifies the account that is owner of the gateway resource. For information
about how to use a wildcard character (*) in a policy, see
Example 2: Allow Read-Only Access to a
To limit permissions for a particular action to a specific gateway only, create a separate statement for
that action in the policy and specify the gateway ID in that statement.
• The second statement grants permissions for the
ec2:DescribeSnapshots
and
ec2:DeleteSnapshot
actions. These Amazon Elastic Compute Cloud (Amazon EC2) actions require
permissions because snapshots generated from Storage Gateway are stored in Amazon Elastic Block
Store (Amazon EBS) and managed as Amazon EC2 resources, and thus they require corresponding EC2
actions. For more information, see
in the
Amazon EC2 API Reference
. Because these Amazon
EC2 actions don't support resource-level permissions, the policy specifies the wildcard character (*) as
the
Resource
value instead of specifying a gateway ARN.
For a table showing all of the Storage Gateway API actions and the resources that they apply to, see
Storage Gateway API Permissions: Actions, Resources, and Conditions Reference (p. 309)
.
Permissions Required to Use the Storage Gateway Console
To use the Storage Gateway console, you need to grant read-only permissions. If you plan to describe
snapshots, you also need to grant permissions for additional actions as shown in the following
permissions policy:
API Version 2013-06-30
300






























